The Biba Model is a fundamental security framework designed to protect data integrity by controlling how information flows within a system. Unlike confidentiality-focused models, Biba's primary goal is maintaining the accuracy and trustworthiness of data—preventing untrusted sources from corrupting critical information and stopping lower-integrity data from contaminating high-integrity systems.
Developed as a direct response to the limitations of Bell-LaPadula, this integrity model complements confidentiality models by addressing a different security concern entirely. While Bell-LaPadula protects secrets from unauthorized disclosure, Biba protects trusted data from unauthorized modification. Understanding this distinction is essential for CISSP candidates, particularly in the Security Architecture and Engineering domain where access control models are frequently tested.
Watch the complete explanation of the Biba Integrity Model with practical examples and CISSP exam tips.
What is the Biba Model?
The Biba Model is a security framework designed to protect data integrity by controlling how information flows within a system. It focuses on one primary goal: maintaining accuracy and trustworthiness of data. This model prevents untrusted sources from corrupting critical information and stops lower-integrity data from contaminating high-integrity systems.
Core Purpose: Integrity Protection
While many security discussions focus on confidentiality—keeping secrets safe from prying eyes—integrity is equally critical in enterprise environments. Consider a financial institution where transaction records must remain accurate, or a hospital where patient medication dosages cannot be altered by unauthorized personnel. In these scenarios, data corruption could have devastating consequences even if no secrets were disclosed.
Integrity ensures data remains accurate, complete, and unmodified by unauthorized sources. Confidentiality ensures data remains secret from unauthorized viewers. The Biba Model exclusively addresses integrity—it has no mechanisms for protecting confidentiality or availability.
The model operates on a simple premise: information should only flow in directions that preserve trust. High-integrity data should never be corrupted by lower-integrity sources, and users should never be influenced by information they cannot trust. This controlled flow forms the foundation of the model's two core rules.
Integrity Levels
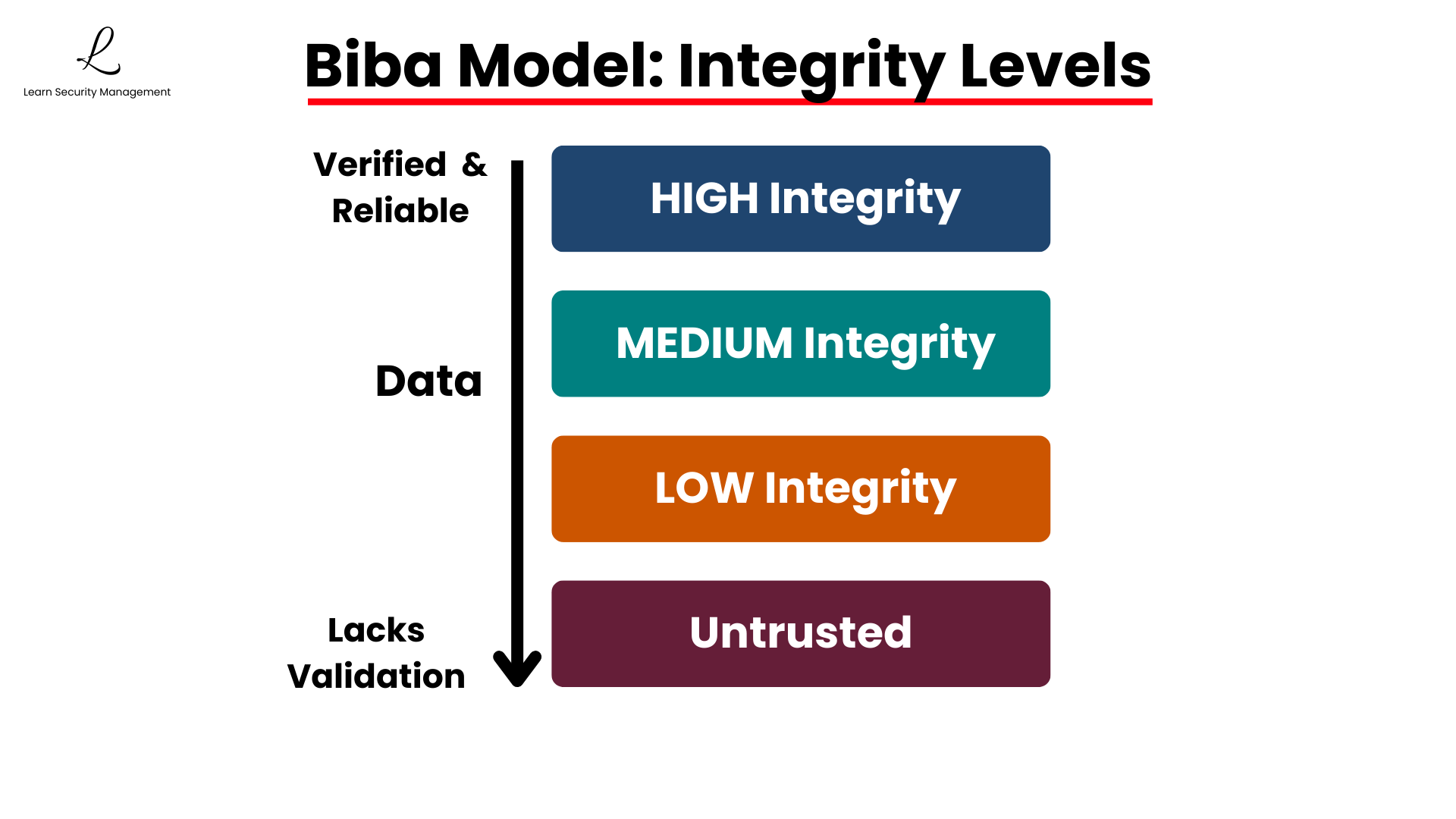
Before diving into the rules, it's essential to understand how Biba organizes information and users through integrity levels. These levels form a hierarchy that determines what data users can modify and what sources they can trust.
The Integrity Hierarchy
The model assigns an integrity level to both data and users. These levels form a hierarchy from top to bottom, typically organized as:
| Integrity Level | Description | Example Data |
|---|---|---|
| High Integrity | Verified, trusted, critical data | Audited financial records, production databases |
| Medium Integrity | Validated internal data | Internal reports, reviewed documents |
| Low Integrity | Unvalidated internal data | Temporary files, draft documents |
| Untrusted | External or unverified data | External vendor data, user input |
Your integrity level determines what data you can modify and what sources you can trust. Think of it like a trust rating—high integrity means the data is verified and reliable, while low integrity or untrusted data hasn't been validated and could contain errors.
Integrity levels reflect the trustworthiness and verification status of data, not its sensitivity or classification. A document can be both highly confidential (sensitive information) and low integrity (unverified content) at the same time. These are independent security properties.
The Two Core Properties
Biba enforces integrity through two fundamental rules that control information flow. These properties work together to ensure that trusted data remains uncorrupted and that decisions are made based on reliable information.
Simple Integrity Property (No Read Down)
The Simple Integrity Property prevents contamination by ensuring you cannot read from lower integrity levels. This is often called the "read up" rule because users can only read from sources at their level or higher—never below.

In practice, this means untrusted or lower-quality data cannot influence critical decisions. The system blocks access to anything that could corrupt your work with unreliable information.
Consider a financial auditor with medium integrity clearance preparing quarterly reports for regulators and investors. If they could pull data from untrusted external sources or low-integrity temporary files, errors or manipulated data could corrupt their analysis. The system blocks access to anything below their integrity level, ensuring they only work with verified, accurate information. They can access high-integrity financial databases and medium-integrity internal reports, but low-integrity temporary files and untrusted spreadsheets from external vendors are completely invisible to them. This matters because one corrupted data point could invalidate an entire audit and lead to regulatory violations.
Star Integrity Property (No Write Up)
The Star Integrity Property (*-Property) prevents corruption by ensuring you cannot write to higher integrity levels. This is often called the "write down" rule because users can only write to their current level or lower—never upward.

In practice, this means lower-integrity users cannot modify critical, trusted data. The system protects high-integrity systems from corruption by less reliable sources.
Imagine a contractor with low integrity access helping with data entry. If they could modify high-integrity production databases directly, mistakes or malicious changes could corrupt systems that thousands of users depend on. The system forces them to write only to low-integrity staging areas. Their work must be reviewed and promoted to higher levels by someone with appropriate authority. A database administrator with high integrity can then validate the data and move it upward. Once information reaches a trusted level, lower-integrity users cannot alter it.
Remember the Biba rules by their opposites to Bell-LaPadula: Biba is "No Read Down, No Write Up" while Bell-LaPadula is "No Read Up, No Write Down." Both use the same structure but protect different properties—Biba protects integrity, Bell-LaPadula protects confidentiality.
Putting It Together: A Banking Example
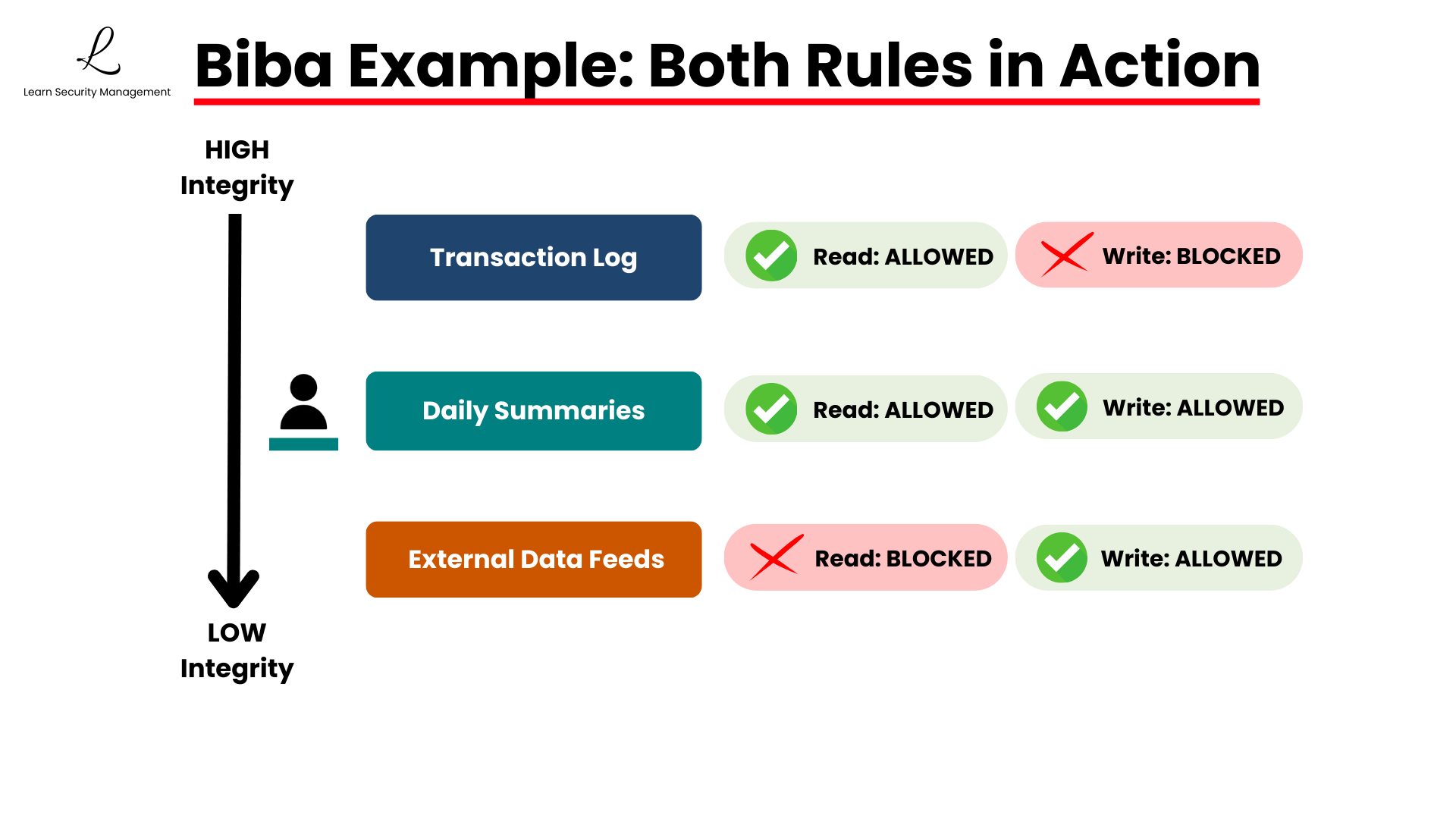
Let's see these rules in action. A bank's core financial system uses Biba to protect transaction records. A junior analyst with medium integrity is reviewing account activity.
Reading (Simple Integrity Property): They can read from high-integrity sources like the verified transaction log and medium-integrity sources like daily summaries. However, they cannot read from low-integrity sources like unverified external data feeds, because that could introduce errors into their analysis.
Writing (Star Integrity Property): When they create their report, they can save it at medium integrity or lower, but they cannot modify the high-integrity master database directly. Their findings must go through a senior analyst with high-integrity access who can verify the information before it updates critical systems.
- Reading: Information flows UP (you read from your level or higher)
- Writing: Information flows DOWN (you write to your level or lower)
- Protection: High-integrity data is protected from both contamination (bad reads) and corruption (bad writes)
Biba vs. Bell-LaPadula Model
Understanding Biba becomes clearer when you compare it to Bell-LaPadula, another fundamental security model. These two models are frequently tested together on the CISSP exam because they represent complementary but opposite approaches to access control.

| Aspect | Biba Model | Bell-LaPadula Model |
|---|---|---|
| Primary Goal | Integrity | Confidentiality |
| Reading Rule | No Read Down (read up only) | No Read Up (read down only) |
| Writing Rule | No Write Up (write down only) | No Write Down (write up only) |
| Protects Against | Data corruption from untrusted sources | Unauthorized disclosure of secrets |
| Typical Use Cases | Financial systems, databases, medical records | Military and classified systems |
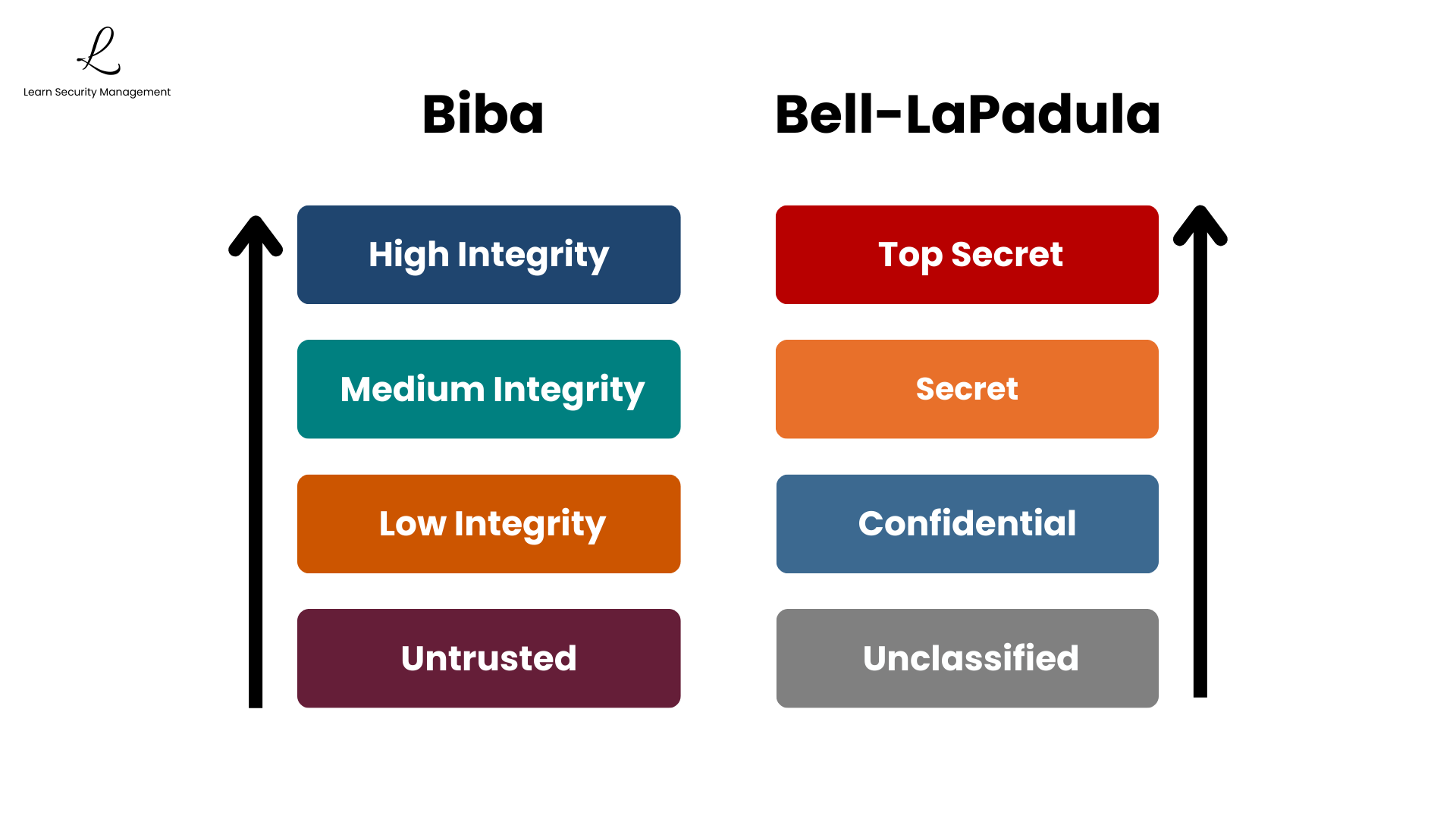
The Fundamental Difference
Here's the fundamental difference: Biba treats higher levels as more trusted and protects them from corruption. Bell-LaPadula treats higher levels as more sensitive and protects them from exposure. They have opposite goals—Biba protects data accuracy, while Bell-LaPadula protects data secrecy.
Consider a hospital's medical records system using Biba. A nurse with medium integrity can read from high-integrity patient records and verified lab results, but cannot read from low-integrity preliminary data that hasn't been confirmed. When documenting patient care, they write to medium-integrity nursing notes but cannot modify high-integrity diagnosis records. The system protects against medical errors and maintains data accuracy.
Now consider a military intelligence database using Bell-LaPadula. An analyst with Secret clearance cannot read Top Secret reports, and when they create documents, they cannot save them to Confidential folders. The system protects against espionage and unauthorized disclosure.
When exam questions describe scenarios with data accuracy, verification, or corruption concerns, think Biba. When they describe scenarios with secrets, classification, or disclosure concerns, think Bell-LaPadula. The security property being protected (integrity vs. confidentiality) determines which model applies.
Practical Limitations
While Biba is theoretically strong for protecting integrity, it has limitations in real-world environments that CISSP candidates should understand.
Key Challenges
| Limitation | Impact | Mitigation |
|---|---|---|
| No Confidentiality Protection | Authorized users could leak sensitive data | Combine with Bell-LaPadula or other controls |
| No Availability Protection | Does not prevent denial of service | Implement separate availability controls |
| Workflow Bottlenecks | Data gets "stuck" at higher levels | Manual review processes for downward flow |
| Classification Discipline | Requires strict integrity labeling | Automated classification and governance |
| Limited Collaboration | Cross-level work is restricted | Defined escalation and review paths |
Single-Focus Design
The model focuses only on integrity and ignores everything else. An authorized user could leak sensitive data to competitors or expose private information—Biba wouldn't stop them because those aren't integrity violations. Organizations typically combine it with other models like Bell-LaPadula for confidentiality or implement additional access controls.
Data Flow Restrictions
The downward-only writing also creates a practical challenge: high-integrity users cannot easily share their work with lower-integrity systems, even when collaboration is necessary. Data often gets stuck at higher integrity levels, requiring manual review processes to move information down when needed.
The Biba Model provides no protection for confidentiality or availability—only integrity. For comprehensive security, organizations must implement multiple complementary controls. Never assume a single security model addresses all requirements.
Security models like Biba provide formal frameworks for specific security properties, but real-world implementations require layered controls addressing confidentiality, integrity, and availability together. No single model provides complete protection.
CISSP Official Study Guide, 9th Edition
Conclusion
The Biba Integrity Model provides a formal framework for protecting data accuracy through controlled information flow. By implementing the Simple Integrity Property (No Read Down) and Star Integrity Property (No Write Up), organizations can prevent untrusted sources from corrupting critical data and ensure that only verified information influences important decisions.
Understanding how Biba differs from confidentiality models like Bell-LaPadula is essential for CISSP candidates. While Bell-LaPadula protects secrets from disclosure using opposite rules (No Read Up, No Write Down), Biba protects trusted data from corruption. These models complement each other in comprehensive security architectures.
For CISSP exam success, focus on understanding the two core properties and their practical applications. Remember that Biba addresses only integrity—organizations must implement additional controls for confidentiality and availability. When exam scenarios involve data accuracy, verification, or corruption prevention, the Biba Model is your answer.
CISSP Practice Tests
Challenge yourself with tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the ChallengeThe Biba Model is a security framework that protects data integrity by controlling information flow. It prevents untrusted sources from corrupting critical data and ensures high-integrity systems remain uncontaminated by lower-integrity information.
The Two Core Properties
- Simple Integrity Property (No Read Down): Users cannot read from lower integrity levels—prevents contamination from untrusted sources
- Star Integrity Property (No Write Up): Users cannot write to higher integrity levels—prevents corruption of trusted data
Integrity Levels
- High Integrity: Verified, audited, critical data (financial records, production databases)
- Medium Integrity: Validated internal data (internal reports, reviewed documents)
- Low Integrity: Unvalidated data (temporary files, drafts)
- Untrusted: External or unverified data (vendor input, user submissions)
Biba vs. Bell-LaPadula
Biba: Protects Integrity → No Read Down, No Write Up → "Higher = More Trusted"
Bell-LaPadula: Protects Confidentiality → No Read Up, No Write Down → "Higher = More Sensitive"
Key Limitations
- Single Focus: Only addresses integrity—no confidentiality or availability protection
- Workflow Bottlenecks: Data can get stuck at higher levels, requiring manual review to flow downward
- Classification Burden: Requires strict discipline in assigning integrity levels
Common Exam Mistakes
- Confusing Biba rules with Bell-LaPadula rules (they are exact opposites)
- Assuming Biba provides confidentiality protection (it does not)
- Forgetting that integrity levels reflect trustworthiness, not sensitivity
- Overlooking that higher integrity in Biba means more trusted, not more secret
The CISSP exam tests your ability to select the correct access control model based on the threat being addressed. Both Biba and Bell-LaPadula are static, rule-based lattice models—but they protect against fundamentally different adversary goals.
1. Identify the Threat Type
The fastest way to distinguish between models is to identify what the adversary is trying to accomplish:
- Sabotage (Corruption/Tampering): The adversary wants to alter, corrupt, or plant false data in trusted systems. This is an integrity attack → Biba
- Espionage (Theft/Disclosure): The adversary wants to steal secrets or view classified information. This is a confidentiality attack → Bell-LaPadula
2. Rule Direction Differences
Both models control read and write operations, but in opposite directions:
- Biba: No Read Down (blocks contamination), No Write Up (blocks corruption)
- Bell-LaPadula: No Read Up (blocks unauthorized viewing), No Write Down (blocks information leakage)
Memory aid: Biba protects the "truth" (integrity) while Bell-LaPadula protects the "secret" (confidentiality).
3. Practical "Manager" Takeaway
As a security manager, you apply these models based on what you're protecting:
- Financial transaction logs → Biba (prevent tampering with audit trails)
- Military intelligence reports → Bell-LaPadula (prevent unauthorized disclosure)
| Look for these Keywords | Think: Biba? |
|---|---|
| "data corruption" or "tampering" | YES |
| "integrity" or "accuracy" | YES |
| "untrusted sources" or "verification" | YES |
| "classified" or "secret" | NO (Bell-LaPadula) |
| "unauthorized disclosure" or "espionage" | NO (Bell-LaPadula) |
Bottom Line: Bell-LaPadula hides the data; Biba protects the truth. If the scenario describes an adversary trying to corrupt or tamper with trusted systems, Biba is your answer.

