Golden Ticket attacks represent one of the most powerful and persistent threats to Active Directory environments, enabling attackers to forge Kerberos Ticket Granting Tickets that grant unlimited domain access. Understanding how these attacks exploit the krbtgt account hash is essential for CISSP candidates preparing for questions on identity management, authentication protocols, and advanced persistent threats within the Identity and Access Management domain.
In this comprehensive guide, we explore the complete anatomy of Golden Ticket attacks, from the prerequisites attackers need to the sophisticated techniques used for ticket forgery. You will learn how to recognize detection challenges, understand why these forged tickets are nearly indistinguishable from legitimate ones, and master the defense strategies that security managers must implement to protect enterprise environments.
Watch the complete video guide on Golden Ticket attacks and enterprise defense strategies.
What is a Golden Ticket Attack?
A Golden Ticket attack involves forging Kerberos Ticket Granting Tickets using a compromised krbtgt account hash. The krbtgt account is a special built-in service account in Active Directory that acts as the service account for the Key Distribution Center itself. This account's password hash is used to encrypt and sign all Ticket Granting Tickets in the domain, making it the master cryptographic key for authentication.
Think of the krbtgt account as the master key to your entire authentication system. When attackers obtain this key, they can create their own "golden tickets" that provide unlimited access to any resource in the domain. These forged tickets are cryptographically valid and indistinguishable from legitimate tickets, making them extremely difficult to detect.
Why "Golden" Tickets?
The term "golden" reflects the supreme value of these tickets to attackers. Unlike stolen user credentials that might be changed or disabled, Golden Tickets provide persistent access that survives password resets, account lockouts, and even user account deletions. They represent the ultimate prize for attackers seeking long-term persistence in an Active Directory environment.
Golden Tickets grant attackers the ability to impersonate any user, including Domain Administrators, without triggering normal authentication events. This persistence mechanism can remain viable for months or years if the organization fails to properly rotate the krbtgt password, making it one of the most dangerous post-exploitation techniques in modern enterprise attacks.

Prerequisites and Attack Path
Critical Prerequisite: Domain Administrative Access
Golden Ticket attacks are post-exploitation techniques, meaning attackers must already have domain administrator or equivalent privileges to extract the krbtgt hash. This is a crucial point for CISSP candidates to understand: Golden Tickets are not an initial attack vector but rather a persistence mechanism used after successful compromise of the domain.
Remember that Golden Ticket attacks require prior administrative compromise. Exam questions may test whether you understand that these attacks are persistence mechanisms, not initial access techniques. The attack chain typically begins with phishing, credential theft, or vulnerability exploitation before attackers can forge Golden Tickets.
Common Attack Paths to Domain Admin
Attackers typically reach domain admin level through several well-documented paths. Phishing campaigns remain the most common method, especially when targeting users with administrative privileges. Once inside the network, attackers use credential theft tools to steal passwords and security tokens, gradually gaining more access through lateral movement until they reach domain admin level.
Exploitation of unpatched vulnerabilities provides another common pathway, particularly zero-day exploits targeting domain controllers or privileged workstations. DCSync attacks using tools like Mimikatz are particularly effective because they request password data directly from domain controllers using normal replication processes that appear completely legitimate to security monitoring systems.
| Attack Path | Description | Detection Difficulty |
|---|---|---|
| Phishing | Targeting privileged users with credential harvesting | Medium |
| Lateral Movement | Progressive privilege escalation across systems | Medium-High |
| Vulnerability Exploitation | Exploiting unpatched systems for admin access | Variable |
| DCSync Attack | Mimicking replication to extract password hashes | High |
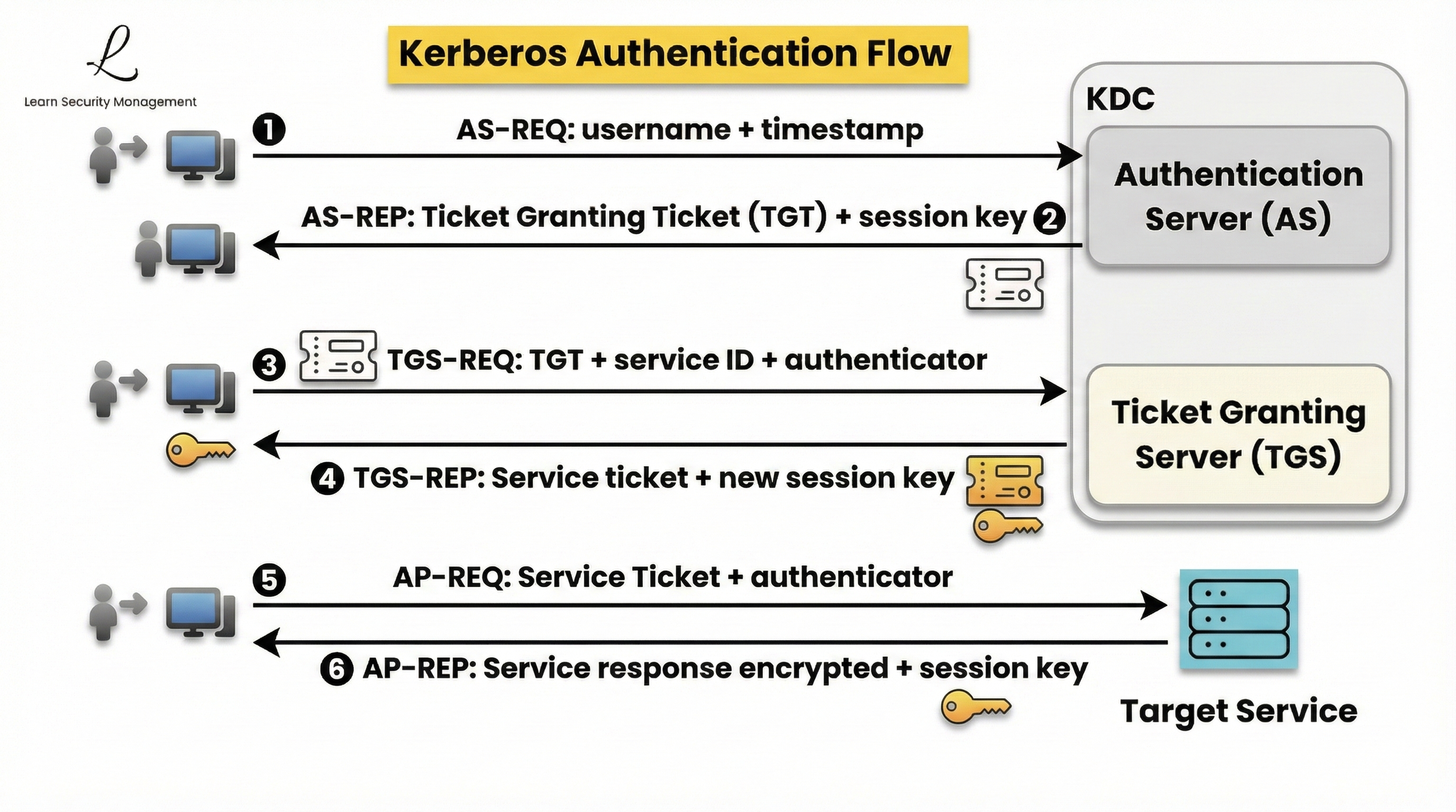
How Golden Ticket Attacks Work
Understanding the execution process of Golden Ticket attacks is essential for both detection and defense. The attack follows a systematic three-step process that transforms stolen cryptographic material into persistent domain access.

Step 1: Information Gathering
Before creating Golden Tickets, attackers must collect essential domain information. They need the domain's fully qualified domain name (FQDN), which identifies the target domain. The domain security identifier (SID) acts as a unique fingerprint for the domain, while the krbtgt NTLM hash is the cryptographic key that validates the forged tickets.

Attackers can impersonate any user identity, including accounts that do not actually exist in Active Directory. This capability makes Golden Tickets particularly dangerous because security teams may see authentication events for users who were never created in the directory.
Step 2: Ticket Forgery
The ticket creation process gives attackers complete control over the forged ticket contents. They can create custom Ticket Granting Tickets with any permissions, setting validity periods for years instead of the normal 8-10 hours. Attackers can include themselves in any security group, including Domain Admins, Enterprise Admins, or Schema Admins.
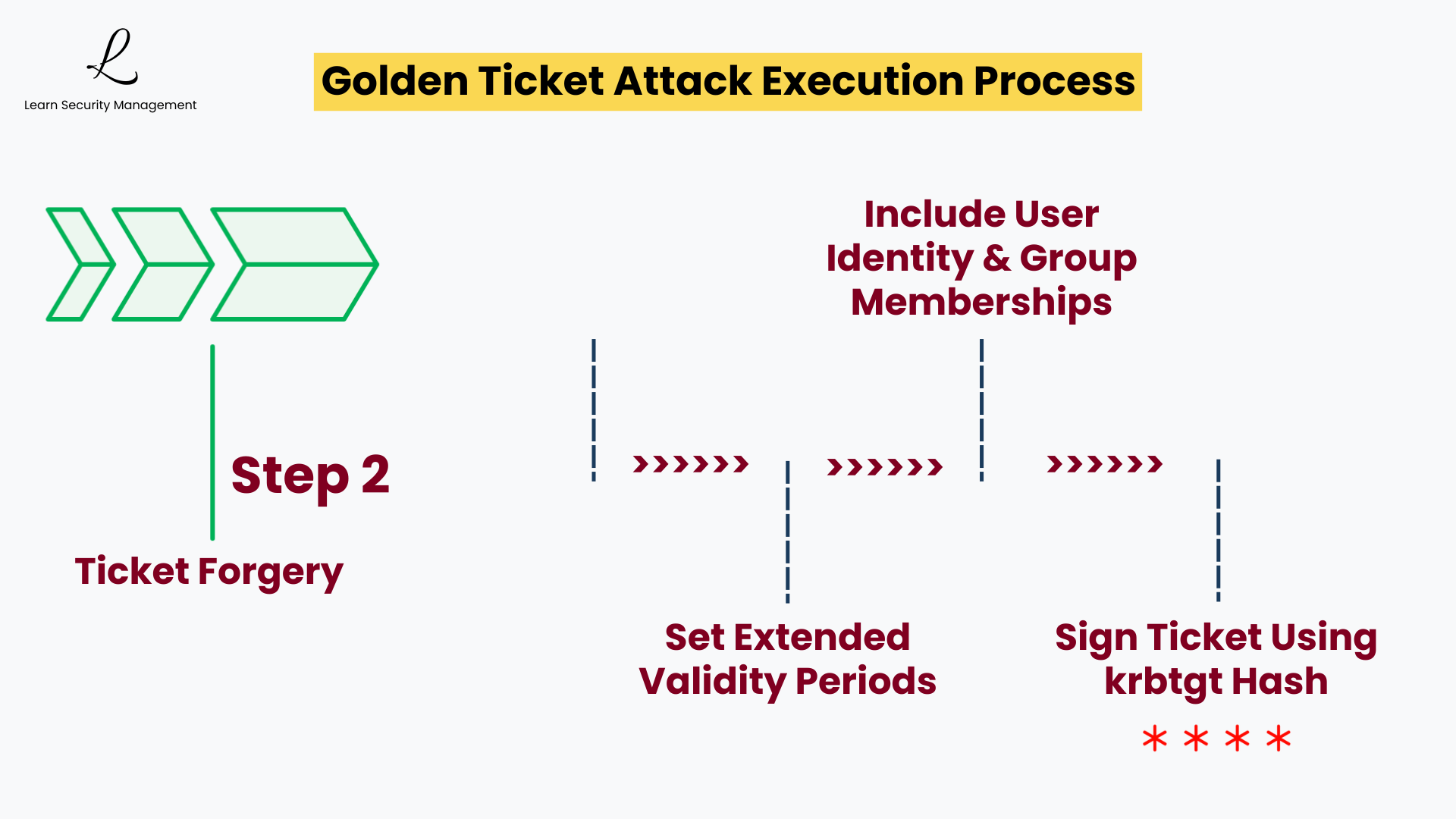
The forged ticket is signed using the stolen krbtgt hash, making it appear completely legitimate to all domain systems. Since the Key Distribution Center uses the same hash to validate tickets, there is no cryptographic method to distinguish forged tickets from genuine ones created through normal authentication.
Step 3: Ticket Injection and Usage
Once Golden Tickets are created, they are injected into the attacker's authentication session. By doing this, the attacker completely bypasses the initial Authentication Service (AS) exchange, meaning they never have to prove their identity or provide a password to the Domain Controller.
However, unlike Silver Tickets (which avoid the DC entirely), the attacker still communicates with the Key Distribution Center (KDC). They present the forged TGT to the Ticket Granting Service (TGS) to request Service Tickets for specific resources. Because the TGT is signed with the valid krbtgt hash, the TGS accepts it without question, allowing the attacker to access any domain resource, create or modify accounts, and exfiltrate data.


- Gather: Collect domain FQDN, SID, and krbtgt hash
- Forge: Create TGT with arbitrary user/group memberships and extended lifetime
- Inject: Load ticket into memory, bypass AS exchange, and request Service Tickets from TGS
Detection Challenges and Indicators
Why Detection is Difficult
Understanding why detection is difficult is fundamental for security professionals. Forged tickets are cryptographically identical to legitimate tickets because they use the same krbtgt hash for signing. Standard Windows security logging does not capture enough detail to identify forged tickets, and native Windows event logs are often insufficient for effective detection.
Organizations typically need third-party SIEM platforms or specialized Identity Threat Detection and Response (ITDR) tools to properly monitor for these attacks. The tickets themselves contain valid signatures that pass all normal authentication checks, making detection extremely difficult without advanced monitoring capabilities that correlate authentication events across the environment.
Golden Tickets bypass the normal authentication flow entirely. Since they do not require contact with the KDC for initial validation, organizations may never see the authentication event that would typically appear when a user logs in. This "silent authentication" is a hallmark of Golden Ticket usage.
Key Detection Indicators
While detecting Golden Tickets is challenging, certain warning signs can reveal their use. Legitimate Ticket Granting Tickets have lifetimes of 8-10 hours, while Golden Tickets often last days, months, or years. Organizations should watch for authentication events involving non-existent or dormant accounts, as attackers sometimes create tickets for fictional users.
Unusual privilege escalations, especially regular users suddenly gaining Domain Admin access without corresponding group membership changes, indicate potential forged tickets. Access patterns inconsistent with normal user behavior, such as a single account accessing resources across multiple geographic locations simultaneously, should trigger immediate investigation.
Advanced Detection Techniques
Advanced detection requires specialized tools and techniques beyond standard Windows logging. Kerberos ticket lifetime analysis monitors for tickets exceeding normal parameters, flagging any TGT with unusual validity periods. Account usage behavioral analysis compares current access patterns against established baselines for each user identity.
| Detection Technique | What It Identifies |
|---|---|
| Ticket Lifetime Analysis | TGTs exceeding normal 8-10 hour validity |
| Behavioral Analysis | Access patterns inconsistent with user profiles |
| Audit Log Correlation | Resource access without corresponding authentication |
| Network Traffic Analysis | Authentication bypassing KDC flows |
Implement continuous monitoring that correlates KDC authentication events with subsequent resource access. When users access resources without a corresponding TGT issuance event from the KDC, this anomaly should trigger automated alerting and investigation workflows.
Mitigation and Defense Strategies
Immediate Response: krbtgt Password Reset
When Golden Ticket attacks are suspected, immediate response through krbtgt password reset is critical. The primary response requires resetting the krbtgt account password twice in succession because Kerberos maintains both current and previous password versions for backward compatibility during normal password rotation.
The first reset invalidates tickets signed with the current password, but tickets signed with the previous password hash remain valid and can still be used by attackers. The second reset must be performed after the maximum ticket lifetimeâ€"typically 10 hoursâ€"to ensure all remaining tickets using the old hash expire naturally before the previous password version is replaced.
The double password reset requirement for krbtgt is a common exam topic. Remember: first reset eliminates current hash usage, second reset (after ticket lifetime expiration) eliminates previous hash usage. Organizations should expect temporary authentication disruptions and plan resets during maintenance windows.
Preventive Security Controls
Prevention focuses on preventing attackers from reaching domain admin level in the first place. The Principle of Least Privilege ensures users have only the minimum access required for their job functions, limiting the blast radius of any compromise. Tiered administrative models separate duties across security boundaries, preventing lateral movement from compromising the entire domain.
Advanced logging and monitoring systems detect suspicious activities before domain admin compromise occurs. Regular Active Directory security audits identify misconfigurations and security weaknesses that attackers could exploit. These audits should specifically examine privileged group memberships, delegation settings, and service account configurations.
Advanced Protection Measures
Modern protection requires advanced security technologies deployed as defense-in-depth layers. Privileged Access Management (PAM) solutions provide just-in-time administrative access with detailed session monitoring, reducing the window during which administrative credentials exist. Endpoint Detection and Response (EDR) tools detect and block credential extraction attempts using behavioral analysis rather than signatures.
Identity Threat Detection and Response (ITDR) solutions focus specifically on identity-based attacks, identifying anomalous authentication patterns that indicate Golden Ticket usage. Zero Trust Architecture continuously verifies user and device identity rather than trusting based on network location, ensuring that even valid-appearing tickets are challenged with additional verification.
Effective protection against Golden Ticket attacks requires multiple security layers working together: preventive controls to stop initial compromise, detective controls to identify attacks in progress, and responsive controls to contain and remediate successful attacks. No single technology provides complete protection.
Organizational Controls
Technical controls must be supported by strong organizational processes. Regular security awareness training prevents initial compromise by teaching employees to recognize phishing and social engineering tactics. Incident response plan testing ensures quick, effective response when attacks are discovered, minimizing attacker dwell time.
Threat hunting programs proactively search for advanced attacks before they achieve their objectives, rather than waiting for automated alerts. Vendor security assessments ensure third-party providers maintain appropriate security standards and do not introduce attack vectors into the environment.
Conclusion
Golden Ticket attacks represent a critical threat to Active Directory environments, exploiting the fundamental trust placed in the krbtgt account to achieve persistent, unlimited domain access. Understanding this attack technique is essential for security professionals and CISSP candidates, as it demonstrates how attackers leverage post-exploitation techniques for long-term persistence.
The security benefits of proper prevention, detection, and response capabilities extend beyond Golden Ticket protection to improve overall Active Directory security posture. Organizations that implement tiered administrative models, deploy advanced detection tools, and maintain tested incident response procedures significantly reduce their risk of domain compromise.
For the CISSP exam, focus on understanding the attack prerequisites, the role of the krbtgt account, detection challenges, and the critical double password reset procedure. Think like a security manager: consider the business impact of these attacks and how organizational controls support technical defenses to create comprehensive protection.
Golden Ticket attacks forge Kerberos TGTs using the compromised krbtgt hash, providing unlimited domain access that bypasses normal authentication. These are post-exploitation persistence mechanisms requiring prior domain admin compromise.
Attack Prerequisites
- Domain Admin Access: Required to extract krbtgt hash
- krbtgt Hash: Master key for encrypting all TGTs
- Domain SID: Unique domain identifier for ticket creation
- Domain FQDN: Fully qualified name of target domain
Attack Execution Steps
- Information Gathering: Collect domain FQDN, SID, and krbtgt hash
- Ticket Forgery: Create TGT with arbitrary permissions and extended lifetime
- Ticket Injection: Load forged TGT, bypass AS exchange, request Service Tickets from TGS
Detection Indicators
- Unusual TGT Lifetime: Tickets valid for days/months instead of 8-10 hours
- Non-existent Users: Authentication for accounts not in AD
- Missing KDC Events: Resource access without corresponding authentication logs
- Anomalous Access: Patterns inconsistent with user behavior profiles
Critical Response: krbtgt Reset
- Double Reset Required: Kerberos maintains two password versions
- Timing Critical: Second reset after max ticket lifetime (10 hours)
- Business Impact: Expect temporary authentication disruptions
Exam Tips
- Golden Tickets are persistence mechanisms, not initial access vectors
- Forged tickets are cryptographically indistinguishable from legitimate TGTs
- Standard Windows logging is insufficient for detection
- Double krbtgt reset is required due to password version history
Exam Focus: The Executive Risk Perspective
Don't just memorize the attack; manage the business impact.
- The Change Management Dilemma: Remediation (the double
krbtgtreset) causes immediate authentication failures. A Security Manager must weigh the certainty of operational downtime against the probability of continued data theft. This is a classic Change Management decision: do you declare an emergency change and disrupt the business, or schedule it and risk the data? - Defensible Security Budget: Native logs are blind to this attack. Use this scenario to justify the ROI for specialized Identity Threat Detection (ITDR) tools. You aren't just buying software; you are buying "Mean Time to Detect" (MTTD) for silent threats.
- The Root Cause Fallacy: If you are fighting a Golden Ticket, you have already lost the battle for Domain Admin. The managerial fix isn't just the password reset; it is enforcing Governance through Tiered Administration to prevent the privilege escalation that made the attack possible.
Challenge Yourself
Tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the Challenge
