Silver Ticket attacks represent one of the most stealthy and dangerous threats to Kerberos-based authentication systems. By forging service tickets using compromised service account password hashes, attackers can gain persistent access to specific services while completely bypassing the Key Distribution Center—making these attacks exceptionally difficult to detect.
In this comprehensive guide, we'll explore how Silver Ticket attacks work, why they're harder to detect than Golden Ticket attacks, and the defense strategies every CISSP candidate needs to understand. Whether you're preparing for the exam or securing enterprise environments, understanding these attacks is essential for protecting Kerberos infrastructure.
Watch the complete video guide on Silver Ticket attacks and Kerberos security
What is a Silver Ticket Attack?
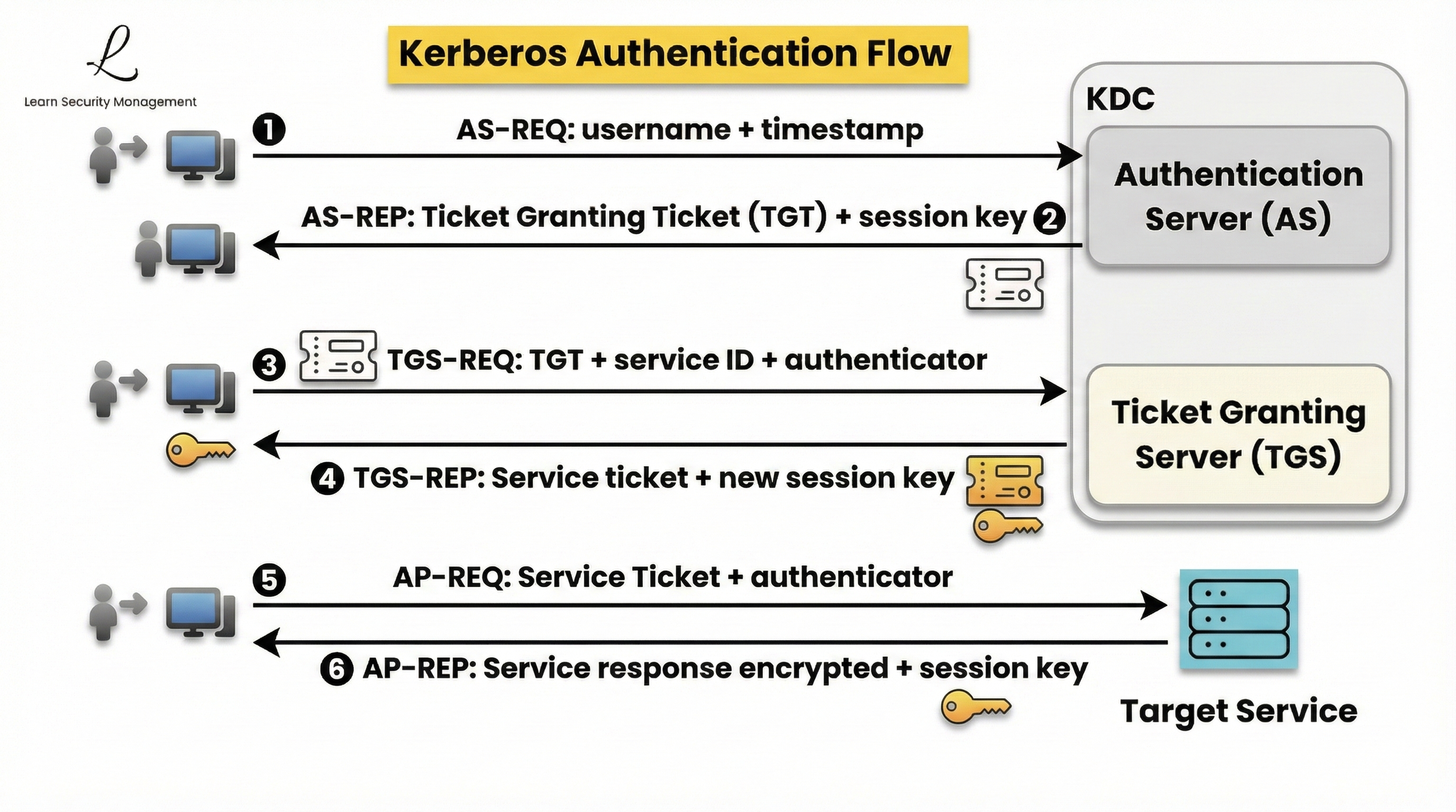
To understand Silver Ticket attacks, it's helpful to first see how Kerberos authentication normally works. In standard Kerberos authentication, a user requests a Ticket Granting Ticket (TGT) from the Authentication Server in steps 1 and 2, then uses that TGT in steps 3 and 4 to request a service ticket from the Ticket Granting Server, which finally allows access to the target service in steps 5 and 6. This process ensures that all authentication is validated by the Key Distribution Center.
A Silver Ticket attack involves forging Kerberos service tickets using a compromised service account password hash. This allows attackers to access specific applications, databases, or network services directly, without interacting with the Key Distribution Center.
Think of a Silver Ticket attack as creating a counterfeit key to a specific room rather than a master key to the entire building. When attackers obtain a service account's password hash, they can forge service tickets that provide direct access to that service without going through normal Kerberos authentication. These forged tickets appear completely legitimate to the target service, enabling persistent, stealthy access.
Why "Silver" Tickets?
The term "silver" reflects both the value and precision of these attacks. Unlike Golden Tickets that provide domain-wide access, Silver Tickets target specific high-value services:
- Target high-value services like databases, file servers, and Exchange
- Provide persistent access until the service password changes
- Operate below the radar of standard Kerberos monitoring
- Require fewer initial privileges than Golden Ticket attacks
Remember that Silver Ticket persistence lasts only until the specific service account password is changed—highlighting why regular password rotation is critical for service accounts. This is a key distinction from Golden Tickets, which persist until the krbtgt account password is reset twice.
Prerequisites and Attack Path
Silver Ticket attacks require fewer privileges than Golden Ticket attacks, making them more accessible to attackers. The primary requirement is obtaining the password hash of a target service account, which can be accomplished through various methods without necessarily achieving domain administrator access. This lower barrier to entry makes Silver Ticket attacks a common post-exploitation technique for maintaining persistence in compromised environments.
Common Attack Paths to Service Account Compromise
Attackers typically obtain service account hashes through several methods:
- Kerberoasting attacks: Specifically target service accounts by requesting service tickets and attempting to crack the encrypted portions offline
- Local credential extraction: Compromising servers where service accounts are running and extracting stored credentials from memory or local storage
- Password spraying: Targeting service accounts with common or weak passwords
- SQL injection attacks: Sometimes reveal database service account credentials stored in connection strings or configuration files
High-Value Target Services
Attackers prioritize certain types of services for Silver Ticket attacks based on the value of data they protect:
- SQL Server databases: Often contain sensitive business data and customer information
- Web application service accounts: May provide access to user data and business logic
- File share services (CIFS/SMB): Can expose confidential documents and intellectual property
- Exchange Server services: Grant access to email communications and calendar information
- Custom enterprise applications: Often contain proprietary business processes and sensitive operational data
Service Principal Names (SPNs) uniquely identify service instances in the Kerberos realm and are essential for proper ticket creation. Attackers use tools like PowerView or BloodHound to enumerate service accounts and their associated SPNs.
How Silver Ticket Attacks Work

Attack Execution Process
Step 1: Service Account Reconnaissance

The first step involves identifying valuable service accounts and their associated Service Principal Names. Attackers gather the following technical requirements:
- Target service account name and domain
- Service Principal Name (SPN) identification
- Service account password hash extraction
- Target service location and configuration
Step 2: Service Ticket Forgery

The second step is where attackers create the malicious tickets. The ticket creation process for Silver Tickets is more focused than Golden Tickets but equally powerful for specific services:
- Create custom service ticket with desired permissions
- Set realistic validity periods to avoid detection
- Include appropriate user identity and group memberships
- Sign ticket using compromised service account hash
Unlike Golden Tickets, which can include any group memberships, Silver Tickets are limited to what the target service recognizes and enforces. The forged ticket is signed using the compromised service account's password hash, making it appear legitimate to the target service.
Step 3: Direct Service Access
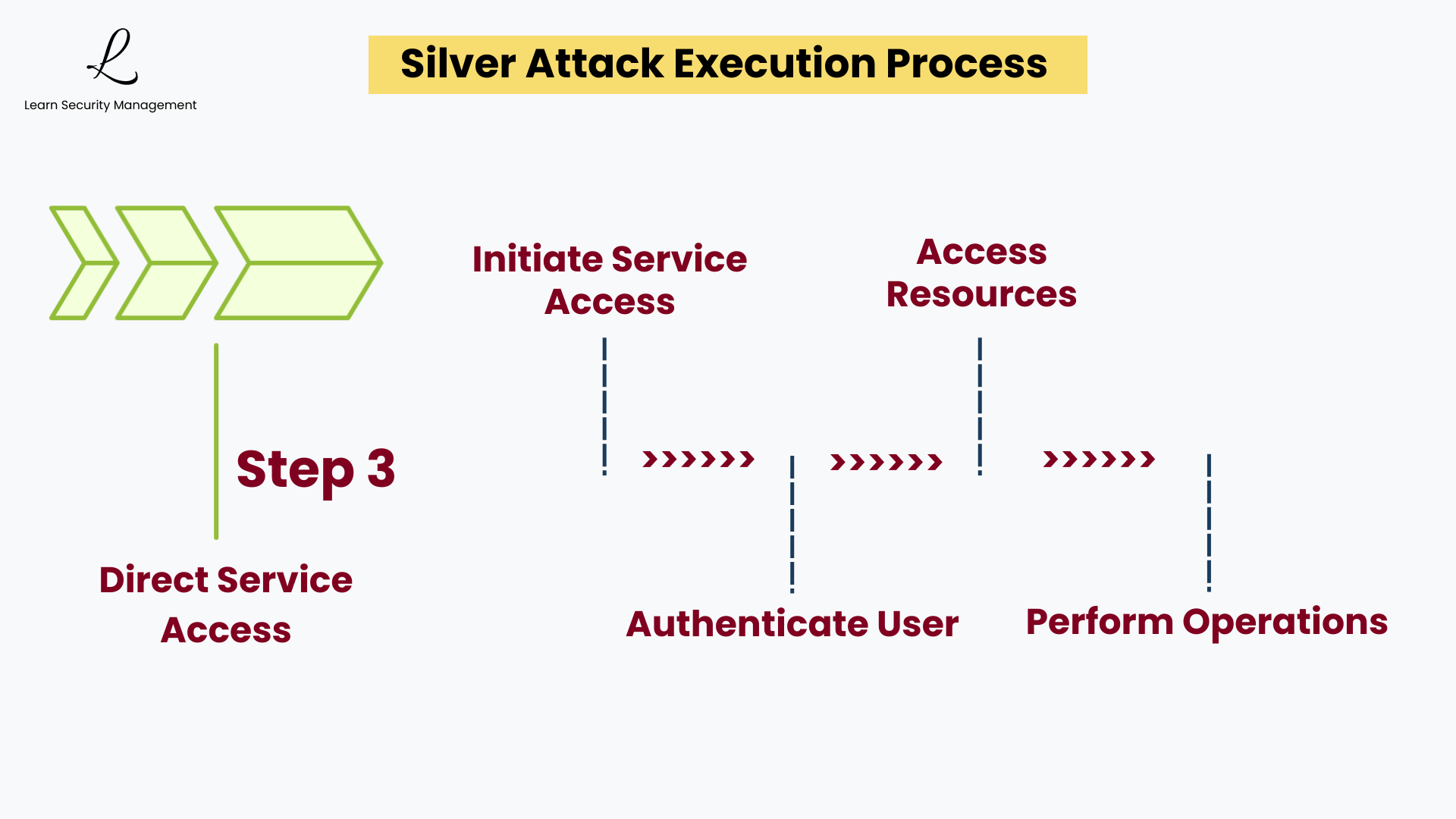
Unlike standard Kerberos authentication, Silver Ticket attacks bypass the KDC entirely after the attacker has obtained the service account hash. Instead of following the normal flow—where a service ticket is requested from the TGS in step 3 and issued in step 4—the attacker forges a valid service ticket and presents it directly to the target service in step 5, skipping the KDC interaction altogether.
Kerberos Steps: Normal vs. Silver Ticket Attack
| Step | Kerberos Action | Silver Ticket Attack Impact |
|---|---|---|
| 1 | AS-REQ: User requests TGT | Not used |
| 2 | AS-REP: AS issues TGT | Not used |
| 3 | TGS-REQ: User requests service ticket | Not used |
| 4 | TGS-REP: TGS issues service ticket | Not used |
| 5 | AP-REQ: User presents service ticket | Attacker presents forged ticket directly |
| 6 | AP-REP: Service responds | Attacker receives normal response |
This table highlights how a Silver Ticket attack subverts the normal Kerberos authentication process. Notice that, unlike standard authentication, the attacker skips the steps involving the Key Distribution Center and interacts directly with the target service. This bypass is what makes Silver Ticket attacks exceptionally hard to detect.
Detection Challenges and Indicators
Why Silver Tickets Are Harder to Detect
Understanding why Silver Tickets are harder to detect is crucial for security professionals. Because Silver Ticket attacks bypass the Ticket Granting Server, there are no TGS-REQ or TGS-REP events recorded in the KDC logs—that's steps 3 and 4 from our authentication flow diagram.
The forged service ticket is simply presented at step 5, making it extremely difficult for traditional monitoring solutions, which rely on KDC logs, to detect unauthorized access. The forged tickets are cryptographically valid for the target service, making them indistinguishable from legitimate service tickets.
Many organizations lack comprehensive service-level authentication monitoring, creating blind spots that attackers exploit. This gap in visibility at the service level is precisely why advanced detection capabilities are so important for modern enterprise security.
Key Detection Indicators
While Silver Tickets are challenging to detect, certain indicators can reveal their presence:
- Service access without corresponding TGS requests: Monitor for service access that doesn't have corresponding Ticket Granting Server requests in KDC logs
- Unusual service account authentication patterns: Access from multiple locations simultaneously or during non-business hours may indicate Silver Ticket usage
- Service tickets with suspicious timing characteristics: Creation and usage times that don't align with normal authentication flows warrant investigation
- Access from unexpected network locations: Access to services from unexpected locations or by users who shouldn't have access should trigger security alerts
Advanced Detection Techniques
Advanced Silver Ticket detection requires monitoring beyond traditional KDC logs:
- Service-level authentication monitoring: Track authentication events at individual services, providing visibility into direct access attempts
- Network traffic analysis: Identify patterns where users access services without normal Kerberos authentication flows
- Behavioral analysis: Monitor for unusual service usage patterns that deviate from established baselines
- Honey pot services: Deploy decoy services that should never be accessed legitimately—any authentication attempts are highly suspicious
Mitigation and Defense Strategies
Immediate Response: Service Account Password Reset
When Silver Ticket attacks are suspected, immediate response through service account password reset is critical. This action immediately invalidates all existing Silver Tickets for those services.
- Identify compromised service accounts: Determine which service accounts are potentially affected
- Coordinate service downtime: Plan for temporary service interruptions with application owners
- Reset service account passwords: Change passwords for suspected compromised accounts
- Update service configurations: Modify all applications and services to use new passwords
Preventive Security Controls
Prevention focuses on reducing the attack surface and limiting the impact of service account compromise:
- Managed Service Accounts (MSAs): Automatically handle password changes and eliminate manual password management
- Regular service account password rotation: Limits the window of opportunity for attackers using compromised hashes
- Service account privilege minimization: Ensures compromised accounts provide access only to necessary resources
- Kerberos delegation restrictions: Prevent service accounts from being used for lateral movement
Implement Group Managed Service Accounts (gMSAs) wherever possible. These accounts automatically rotate passwords every 30 days and can be used across multiple servers, significantly reducing the attack window for Silver Ticket attacks.
Advanced Protection Measures
Modern protection requires comprehensive service account security:
- Service account monitoring: Track authentication patterns and usage to identify anomalies
- Privileged Access Management (PAM): Provide controlled access to service accounts with detailed session monitoring
- Just-in-time access: Provide temporary service access credentials instead of persistent service accounts
- Network segmentation: Isolate critical services from general network access, limiting the impact of compromised service accounts
Organizational Controls
Technical controls must be supported by strong organizational processes:
- Service account inventory management: Maintain accurate records of all service accounts, their purposes, and access requirements
- Regular security assessments: Identify weak or unnecessary service accounts that increase attack surface
- Incident response procedures: Ensure quick detection and response to service account compromise
- Security awareness training: Help administrators recognize and respond to potential Silver Ticket attacks
Silver Ticket vs. Golden Ticket Comparison
Understanding the practical differences between Silver and Golden Ticket attacks helps security professionals prioritize their defense strategies.
| Attribute | Silver Ticket | Golden Ticket |
|---|---|---|
| Privilege Required | Service account hash | krbtgt account hash (Domain Admin) |
| Access Scope | Specific service only | Domain-wide access |
| Detection Difficulty | Harder (no KDC logs) | Easier (KDC interaction logged) |
| Persistence Duration | Until service password change | Until krbtgt password reset (twice) |
| KDC Interaction | None (bypassed completely) | Required for TGS requests |
| Attack Complexity | Lower initial barrier | Requires domain compromise |
Silver Tickets require lower initial privileges but provide more focused access, making them suitable for targeted attacks on specific services. Golden Tickets require higher privileges but offer broader access across the domain. Silver Tickets are often harder to detect because they don't interact with the Key Distribution Center, while Golden Tickets leave more traces in authentication logs.
Core Concepts
- Silver Ticket: Forged Kerberos service ticket using compromised service account hash
- KDC Bypass: Attack skips steps 1-4 of Kerberos, presenting forged ticket directly at step 5
- Service-Specific Access: Unlike Golden Tickets, provides access only to the targeted service
Attack Requirements
- Service account password hash: Obtained via Kerberoasting, credential extraction, or password attacks
- Service Principal Name (SPN): Identifies the target service in Kerberos realm
- Domain SID: Security identifier for the domain
Detection Challenges
- No KDC logs: TGS-REQ/TGS-REP events not generated (steps 3-4 bypassed)
- Cryptographically valid: Forged tickets appear legitimate to target services
- Service-level monitoring required: Traditional KDC monitoring insufficient
Key Mitigations
- Managed Service Accounts (MSAs/gMSAs): Automatic password rotation every 30 days
- Service account password reset: Immediately invalidates existing Silver Tickets
- Service-level authentication monitoring: Track authentication at individual services
- Honey pot services: Detect unauthorized access attempts
Exam Tips
- Remember: Silver Tickets target specific services; Golden Tickets provide domain-wide access
- Common mistake: Thinking KDC logs can detect Silver Tickets—they cannot because KDC is bypassed
- Focus on: Silver Tickets require less privilege than Golden Tickets but have narrower scope
- Key distinction: Persistence ends with service password change (Silver) vs. krbtgt reset twice (Golden)
Challenge Yourself
Tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the Challenge
