Kerberoasting is a sophisticated attack technique that enables any authenticated domain user to extract and crack service account passwords offline, making it one of the most dangerous credential theft methods in Active Directory environments. Understanding how attackers exploit the Kerberos authentication process to target service accounts is essential for CISSP candidates preparing for questions on identity management, authentication protocols, and enterprise security within the Identity and Access Management domain.
In this comprehensive guide, we explore the complete anatomy of Kerberoasting attacks, from the minimal prerequisites attackers need to the systematic process of extracting and cracking service tickets. You will learn why these attacks are particularly effective, understand the detection challenges security teams face, and master the defense strategies that security managers must implement to protect service accounts in enterprise environments.
Watch the complete video guide on Kerberoasting attacks and enterprise defense strategies.
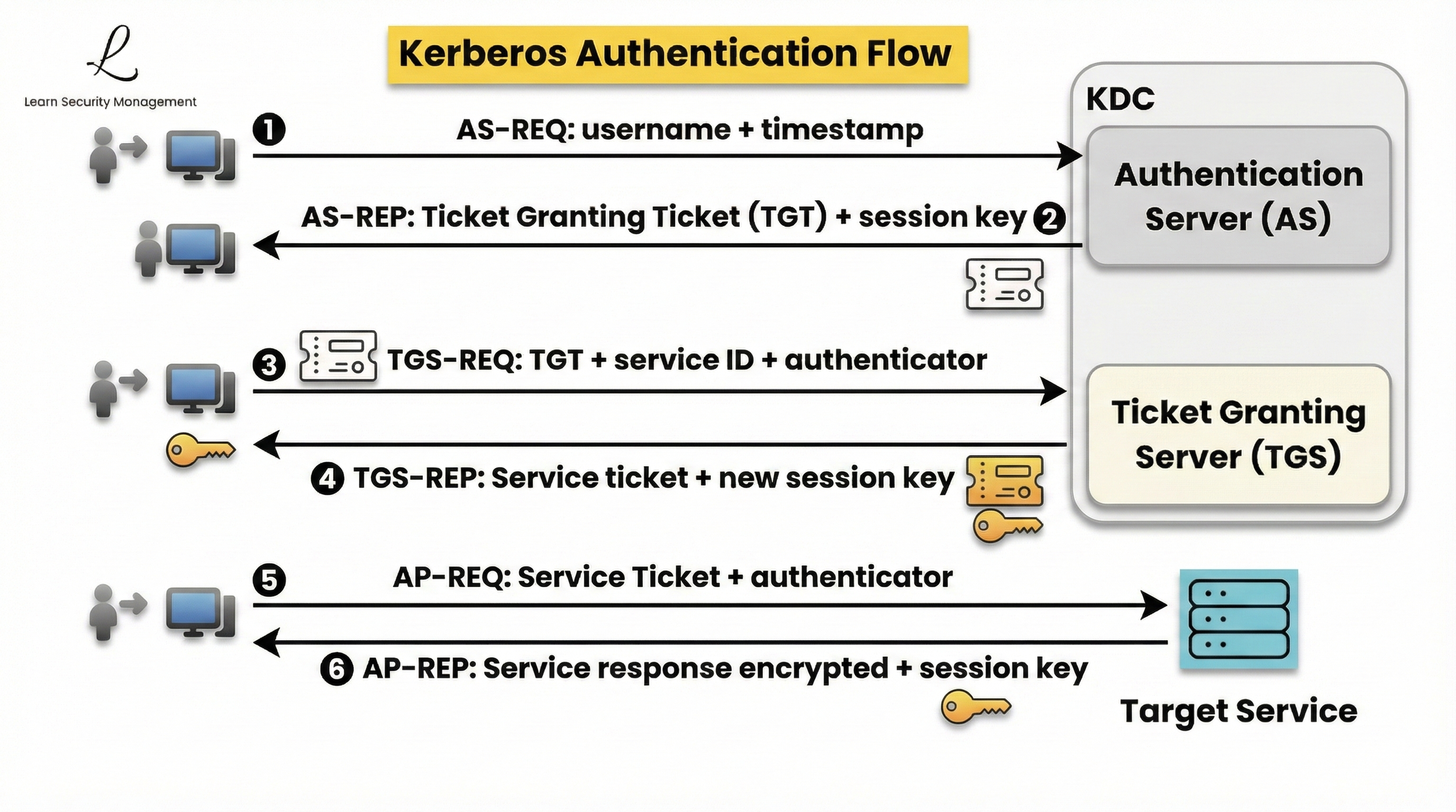
What is Kerberoasting?
Kerberoasting is an attack technique where any authenticated domain user can exploit steps 3 and 4 of the normal Kerberos authentication process. Attackers send TGS-REQ requests to obtain service tickets for accounts with Service Principal Names (SPNs). The Ticket Granting Server responds with tickets encrypted using the service account's password hash. Attackers extract these tickets and attempt to crack them offline to recover the plaintext passwords.
Think of Kerberoasting as asking for a locked box you know contains valuable information, then taking that box somewhere private to figure out the combination. In Kerberos, this "locked box" is the service ticket. Because the service ticket is encrypted with the service account's password hash, attackers can use offline password cracking tools to recover the actual password—often for accounts with high privileges and weak or unchanged credentials.
Why Kerberoasting is Effective
Kerberoasting is remarkably effective because it leverages legitimate Kerberos operations and requires no special privileges—any domain user can perform it. Since the password cracking happens offline, there is no network activity to alert security teams during the cracking phase. Service accounts are particularly attractive targets because they often have weak or unchanged passwords and high levels of access, making successful attacks especially damaging.
Unlike attacks that forge tickets like Golden Tickets, Kerberoasting relies on standard Kerberos requests, making it difficult to distinguish from normal user activity. The real danger comes after successful password recovery: attackers gain direct access to services, often with elevated privileges, without triggering additional security alerts.
Remember that Kerberoasting requires only standard domain user privileges—this is a crucial distinction from Golden Ticket attacks which require domain admin access. Exam questions may test whether you understand the different privilege requirements for various Kerberos-based attacks.
Prerequisites and Attack Requirements
Minimal Attack Prerequisites
Kerberoasting has remarkably low prerequisites compared to other advanced attacks. Attackers need only authenticated domain access, which is often gained through phishing campaigns or password spraying attacks. Once inside the domain, they identify high-value service accounts like SQL databases, web applications, and file shares, then use standard tools to request service tickets.
| Requirement | Description | Difficulty to Obtain |
|---|---|---|
| Domain User Account | Any authenticated domain credentials | Low |
| Network Access | Ability to communicate with Domain Controller | Low |
| SPN Enumeration | Identifying accounts with Service Principal Names | Low |
| Cracking Resources | Computing power for offline password cracking | Low-Medium |
No elevated privileges are required for Kerberoasting, making this an attractive early-stage attack for gaining additional credentials. The attack can be performed by any domain user, including users with minimal access rights.
How Kerberoasting Attacks Work
Understanding the execution process of Kerberoasting attacks is essential for both detection and defense. The attack follows a systematic four-step process that transforms normal Kerberos ticket requests into a credential theft opportunity.
Step 1: Service Account Enumeration
Attackers first identify service accounts by querying Active Directory for accounts with Service Principal Names. They focus on high-value targets such as SQL Server service accounts, web applications, and file shares, prioritizing accounts that might provide access to sensitive data or enable lateral movement across the network.

Step 2: Service Ticket Request
Once targets are identified, attackers request service tickets using the standard Kerberos protocol. These requests appear completely legitimate because they use normal authentication mechanisms. Attackers often target multiple service accounts simultaneously to maximize their chances of success, requesting tickets for all discovered SPNs.
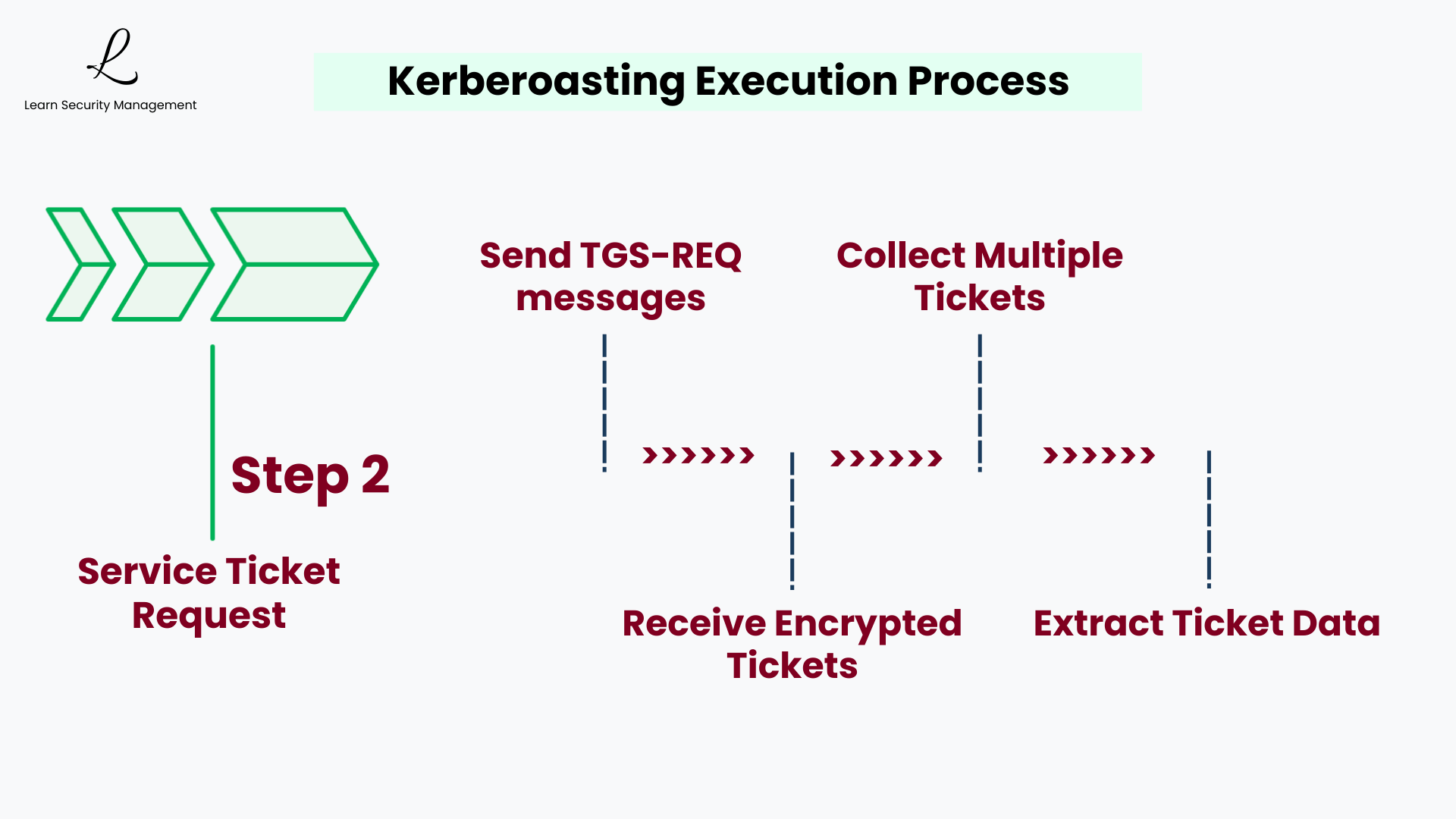
The service ticket request is indistinguishable from legitimate user activity because attackers are using the exact same Kerberos protocol mechanisms that normal users employ. The Domain Controller has no way to determine the requester's intent—it simply fulfills valid authentication requests.
Step 3: Offline Password Cracking
The offline password cracking phase is where attackers invest the most effort. They use various methods including dictionary attacks with common passwords, brute force attempts against shorter passwords, and hybrid approaches combining wordlists with rule-based mutations. The success of this phase depends heavily on the strength of the target service account passwords.

Weak or unchanged passwords are particularly vulnerable to cracking. Service accounts created years ago with simple passwords, or accounts that have never had password rotation enforced, can often be cracked within minutes or hours depending on available computing resources.
Step 4: Credential Validation and Exploitation
After successfully cracking service account passwords, attackers validate the credentials and assess their access scope. Compromised service accounts often provide pathways for lateral movement, access to sensitive databases, and opportunities for establishing persistence within the network. The attacker can now authenticate directly as the service account.
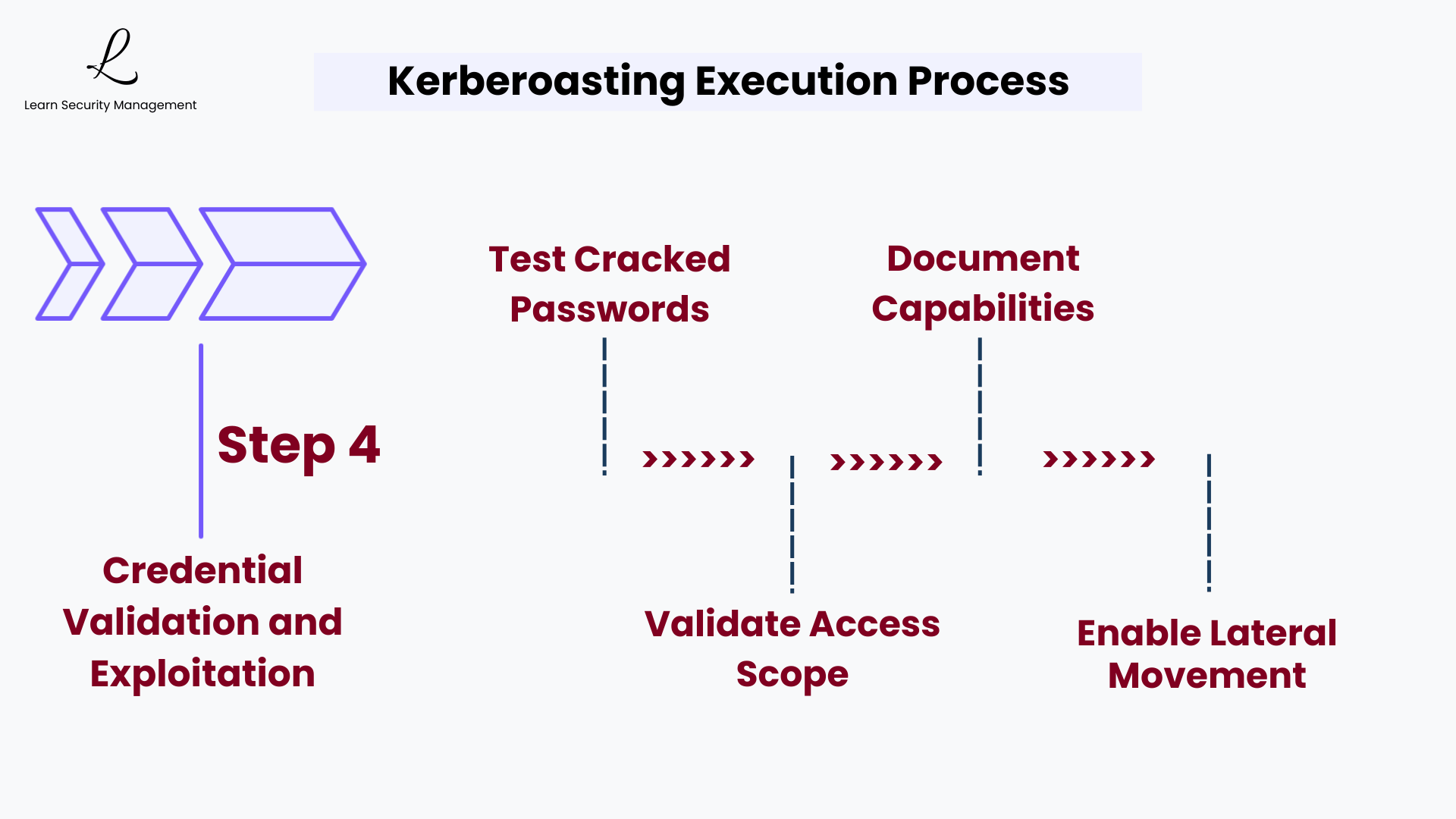
Organizations should assume that any service account with a weak password has already been compromised through Kerberoasting. Proactive password strength auditing and rotation are essential defense measures.
Detection Challenges and Indicators
Why Kerberoasting is Difficult to Detect
Kerberoasting is hard to detect because it uses normal Kerberos requests that appear identical to legitimate user activities. The offline password cracking occurs outside the target network, leaving minimal forensic evidence. Many organizations lack comprehensive Kerberos monitoring capabilities, creating blind spots that attackers exploit repeatedly.
Unlike Golden Ticket attacks that bypass authentication entirely, Kerberoasting uses standard authentication flows. This makes baseline behavior analysis crucial for detection—you cannot simply look for protocol anomalies because the protocol usage is completely normal.
Key Detection Indicators
While challenging to detect, certain behavioral indicators can reveal attack activity when proper monitoring is in place:
- Unusual Patterns: Multiple service ticket requests in rapid succession from a single account
- High Volume: Requests for many different services from accounts that typically access few resources
- Timing Anomalies: Service ticket requests occurring outside normal business hours
- Atypical Access: Requests for services that the user has never accessed before
- RC4 Encryption: Requests specifically for RC4-encrypted tickets (weaker encryption, easier to crack)
Effective Kerberoasting detection requires establishing baseline behavior for service ticket requests and alerting on deviations. Focus on monitoring Event ID 4769 (Kerberos Service Ticket Operations) and look for patterns of bulk ticket requests, especially those requesting RC4 encryption.
Mitigation and Defense Strategies
Immediate Response and Prevention
The primary defense against Kerberoasting focuses on securing service accounts. Reset passwords immediately for accounts showing suspicious activity, though coordinate with application owners to prevent service disruptions. Implement strong password policies requiring complex passwords of 25 characters or more for service accounts.
| Defense Measure | Implementation | Effectiveness |
|---|---|---|
| Strong Passwords | 25+ character complex passwords for service accounts | High |
| Managed Service Accounts | Use Managed Service Accounts for automatic password rotation | High |
| AES Encryption | Disable RC4 encryption, enforce AES-256 | Medium-High |
| Privilege Minimization | Reduce service account permissions to minimum required | Medium |
| Monitoring | Alert on bulk service ticket requests | Medium |
Advanced Protection Measures
Modern protection requires comprehensive monitoring of service account authentication patterns and implementing Privileged Access Management (PAM) solutions for controlled access. Network segmentation isolates critical services, while regular security assessments including Kerberoasting simulations help identify vulnerable accounts before attackers do.
Managed Service Accounts automatically handle password changes, effectively eliminating the Kerberoasting threat for covered services. This should be the default for all new service deployments.
Kerberoasting vs. Other Kerberos Attacks
Understanding how Kerberoasting compares to other Kerberos-based attacks helps security professionals prioritize defenses and recognize attack patterns:
| Attack Type | Prerequisites | Target | Impact |
|---|---|---|---|
| Kerberoasting | Any domain user | Service account passwords | Service access, lateral movement |
| Silver Ticket | Service account hash | Specific service access | Persistent service access |
| Golden Ticket | Domain Admin (krbtgt hash) | Entire domain | Complete domain control |
Kerberoasting is the most accessible attack, requiring only standard user access. Success may enable Silver Ticket attacks if service account hashes are obtained. Golden Tickets require the highest privileges but provide the most extensive access. Understanding this progression helps defenders prioritize protective controls.
Conclusion
Kerberoasting represents a critical threat to Active Directory environments, exploiting the fundamental design of Kerberos authentication to enable offline password cracking attacks against service accounts. Understanding this attack technique is essential for security professionals and CISSP candidates, as it demonstrates how attackers leverage normal authentication mechanisms for credential theft.
The security benefits of proper service account hardening extend beyond Kerberoasting protection to improve overall Active Directory security posture. Organizations that implement strong password policies, deploy Managed Service Accounts, and maintain comprehensive monitoring significantly reduce their exposure to credential-based attacks.
For the CISSP exam, focus on understanding that Kerberoasting requires only standard user privileges, the role of Service Principal Names, detection challenges related to legitimate protocol usage, and the effectiveness of Managed Service Accounts as a defense. Think like a security manager: consider how organizational controls around service account governance support technical defenses to create comprehensive protection.
Kerberoasting exploits normal Kerberos authentication to extract service tickets encrypted with service account password hashes, enabling offline password cracking. Unlike Golden Tickets, Kerberoasting requires only standard domain user privileges.
Attack Prerequisites
- Domain User Access: Any authenticated domain account
- SPN Enumeration: Ability to query Active Directory for service accounts
- Cracking Resources: Computing power for offline password attacks
- No Elevated Privileges: Standard user rights are sufficient
Attack Execution Steps
- Service Account Enumeration: Query AD for accounts with SPNs
- Service Ticket Request: Request TGS tickets for identified services
- Offline Cracking: Extract tickets and attempt password recovery
- Credential Exploitation: Validate and use recovered passwords
Detection Indicators
- Bulk Ticket Requests: Multiple TGS requests from single account
- RC4 Preference: Requests specifically for weaker encryption
- Timing Anomalies: Requests outside normal business hours
- Atypical Access: Requests for services user never accesses
Key Defense Measures
- Strong Passwords: 25+ character complex passwords for service accounts
- Managed Service Accounts: Automatic password rotation for service accounts
- AES Enforcement: Disable RC4, require AES-256 encryption
- Privilege Minimization: Reduce service account permissions
Exam Tips
- Kerberoasting requires only standard user privileges—key distinction from Golden Tickets
- Offline cracking leaves no network evidence during the attack phase
- Managed Service Accounts: Effectively eliminate this attack vector
- Detection relies on behavioral analysis, not protocol anomalies
Exam Focus: The Executive Risk Perspective
Don't just memorize the attack; manage the business impact.
- The Low Barrier Problem: Unlike Golden Ticket attacks requiring domain admin, Kerberoasting can be performed by anyone with a compromised user account. This means your attack surface includes every phishing victim and every weak password—a risk that demands strong user security awareness programs.
- Technical Debt as Security Debt: Legacy service accounts with weak, unchanged passwords represent accumulated technical debt that translates directly to security risk. The managerial solution is establishing service account governance with mandatory rotation and strength requirements.
- The Managed Service Account Business Case: Managed Service Accounts eliminate Kerberoasting risk entirely while reducing operational overhead for password management. Frame the migration as both a security improvement and an operational efficiency gain.
Challenge Yourself
Tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the Challenge
