The Clark-Wilson Model is the gold standard for commercial data integrity. Unlike models that focus primarily on confidentiality or preventing unauthorized disclosure, Clark-Wilson addresses the real-world challenge businesses face every day: ensuring that data remains accurate, consistent, and protected from both accidental corruption and deliberate fraud.
This model is essential knowledge for CISSP candidates because it bridges the gap between theoretical access control and practical business requirements. Understanding how Clark-Wilson's two core mechanisms, well-formed transactions and separation of duties, work together to protect data integrity is crucial for exam success and real-world security architecture.
Watch the complete explanation of the Clark-Wilson Model with practical examples and CISSP exam tips.
What is the Clark-Wilson Model?
The Clark-Wilson Model is a security framework specifically designed to protect data integrity in commercial environments. Published in 1987 by David D. Clark and David R. Wilson, this model addresses a fundamental business requirement: ensuring that critical data such as financial records, inventory counts, and transaction logs remains accurate and trustworthy.
Core Purpose: Commercial Data Integrity
While Bell-LaPadula focuses on confidentiality and Biba focuses on integrity through classification levels, Clark-Wilson takes a distinctly commercial approach. It recognizes that in business environments, the greatest threat to data integrity often comes from authorized users, employees who have legitimate access but might make errors or commit fraud. The model addresses both risks through its dual mechanisms.
The Clark-Wilson Model protects integrity through two complementary properties: Certification ensures that procedures maintain data validity (through well-formed transactions), while Enforcement controls who can execute those procedures (through separation of duties). Together, these prevent both accidental corruption and intentional fraud.
What makes Clark-Wilson unique is its focus on indirect access. Users never interact with data directly. Instead, all modifications must go through preapproved procedures that enforce business rules and maintain data consistency. This procedural approach mirrors how real businesses operate, where transactions follow defined processes rather than ad hoc database edits.
Classifying Data for Protection
Clark-Wilson begins by classifying data into two categories based on how critical it is to protect. This classification determines which data requires strict integrity controls and which data can be handled more freely.
Constrained Data Items (CDIs)
Constrained Data Items are the protected data assets that must maintain integrity at all times. These are the critical business records subject to integrity controls and auditing. Examples include bank account balances, inventory records, payroll data, and financial transactions.
CDIs are constrained because they can only be modified through approved procedures, never directly. A bank account balance is a CDI because errors cause financial loss and regulatory liability. Inventory records are CDIs because incorrect counts lead to stock shortages or waste. The key characteristic of CDIs is that they represent data the organization cannot afford to have corrupted.
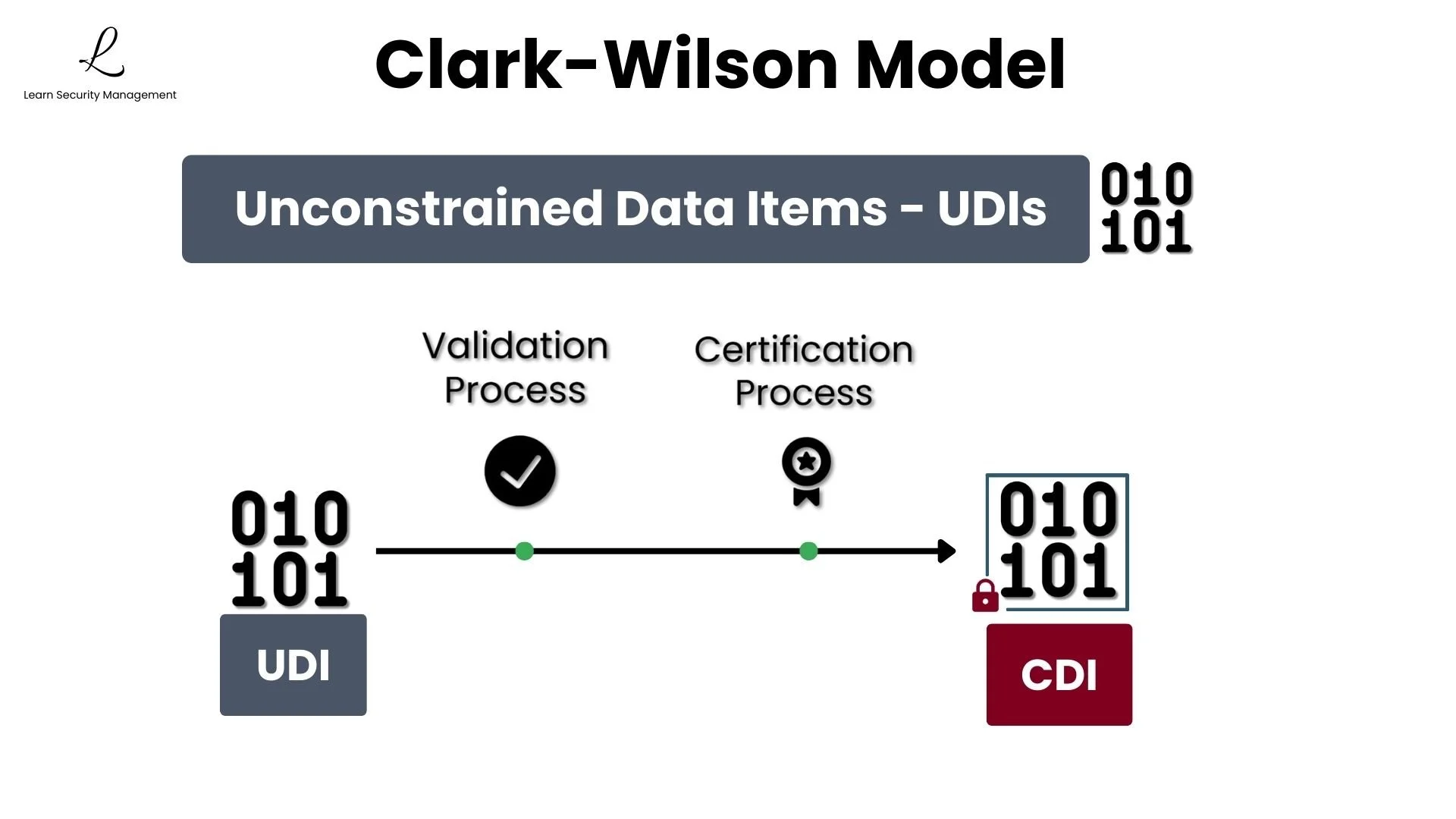
Unconstrained Data Items (UDIs)
Unconstrained Data Items are data that exists outside the security model's integrity controls. These items can be modified freely without integrity checks and include things like draft documents, user uploads, and external data feeds that haven't been validated.
When a UDI needs to become trusted data, it must go through a validation and certification process before becoming a CDI. For example, a customer's uploaded spreadsheet (UDI) must be validated, verified against business rules, and formally accepted before its data can update inventory records (CDI).
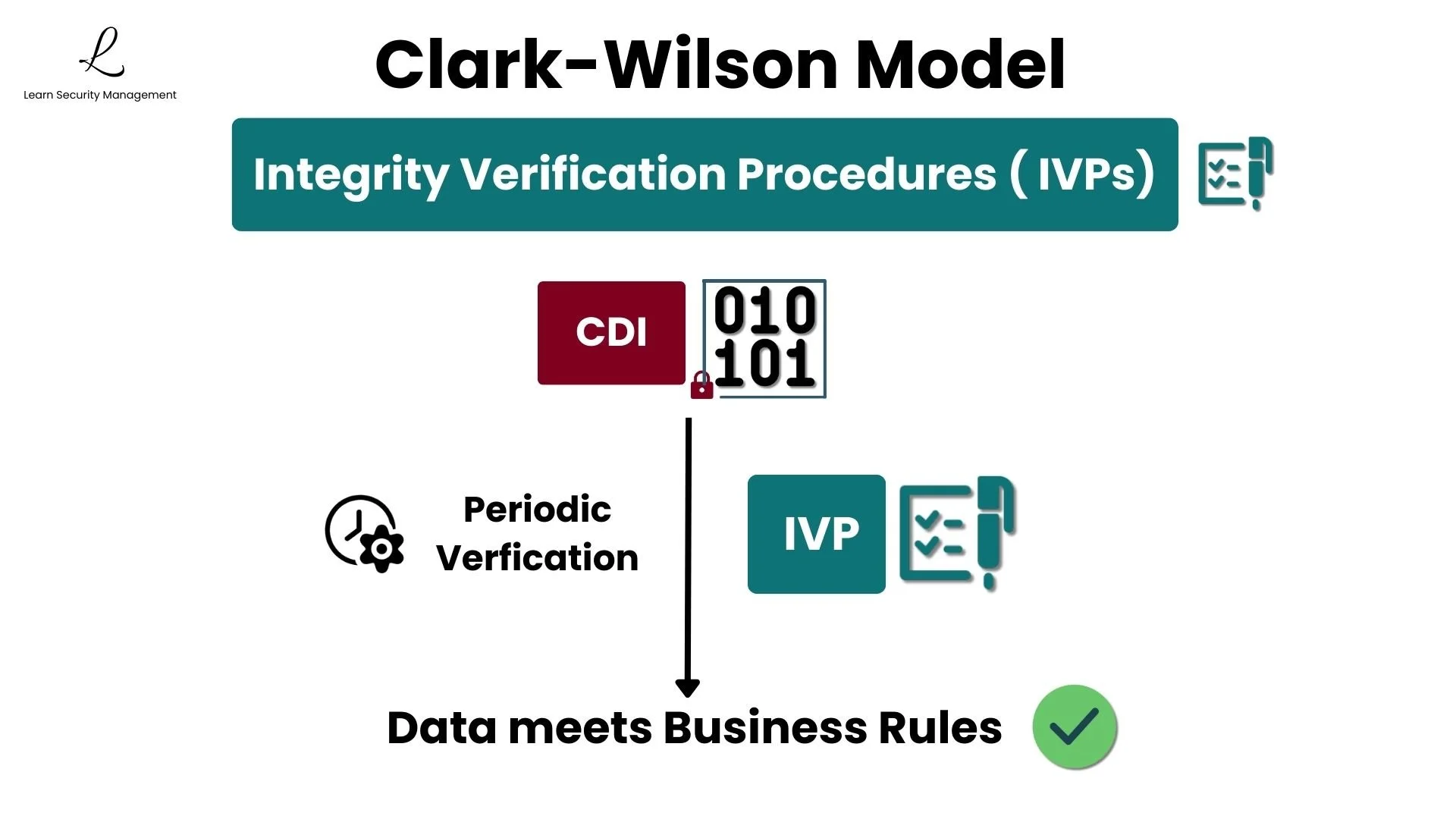
Integrity Verification Procedures (IVPs)
Once data becomes a CDI, how do we ensure it stays accurate? Clark-Wilson uses Integrity Verification Procedures. IVPs are automated checks that validate CDIs are in a valid state, running periodically or after transactions to confirm data meets business rules.
An IVP might confirm that bank account balances are non-negative, that inventory quantities match physical counts, or that debits equal credits across related accounts. When problems are detected, they're flagged for review before errors can propagate through the system.
Controlling How Data Changes
IVPs verify that data is correct, but how do we ensure changes don't corrupt it in the first place? This is where Transformation Procedures come in, the heart of Clark-Wilson's integrity protection.
Transformation Procedures (TPs)
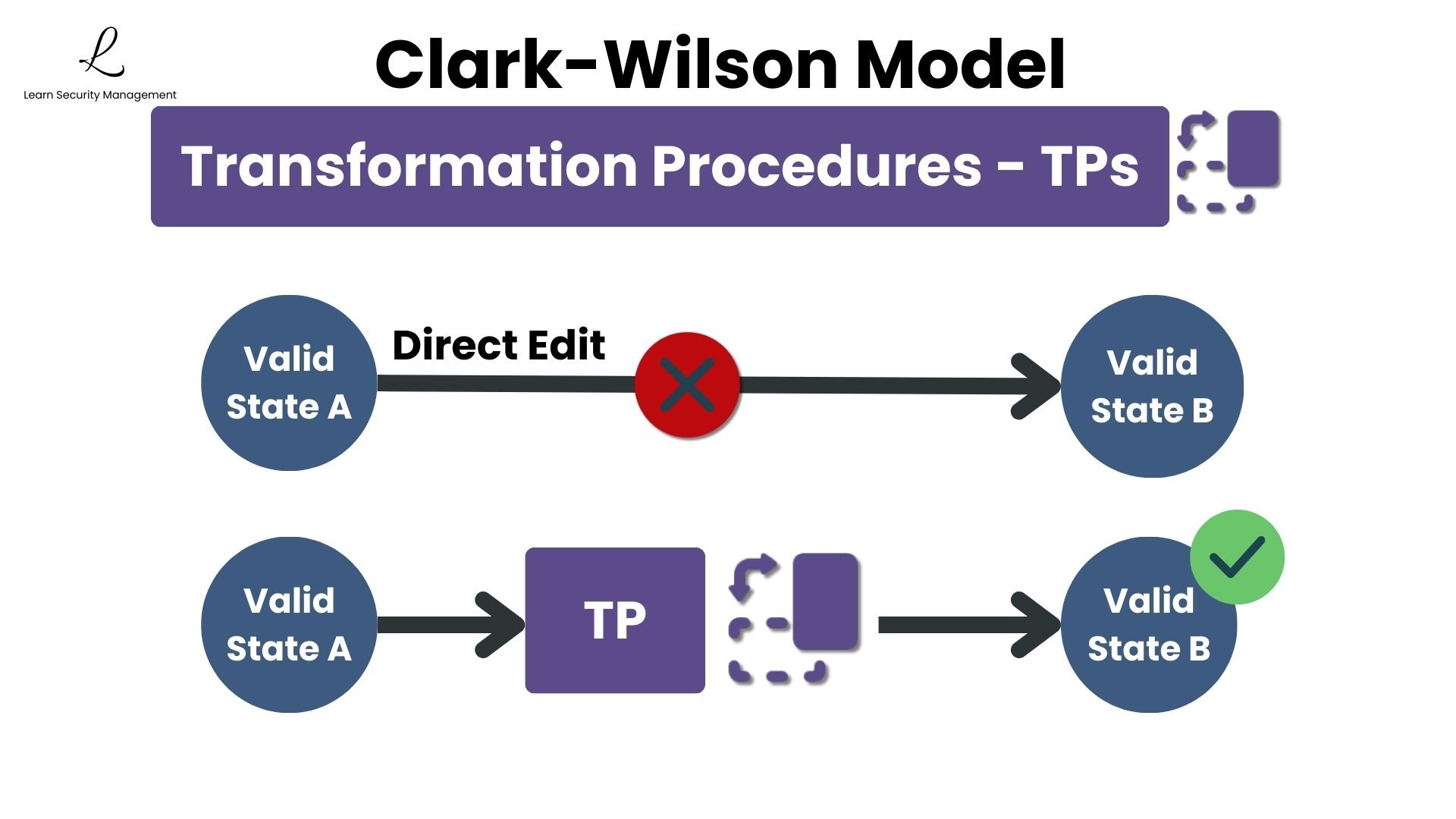
Clark-Wilson forbids direct access to CDIs. Users cannot simply open a database and edit values. Instead, every modification must go through a Transformation Procedure, a certified program or process that enforces all business rules and maintains data integrity.
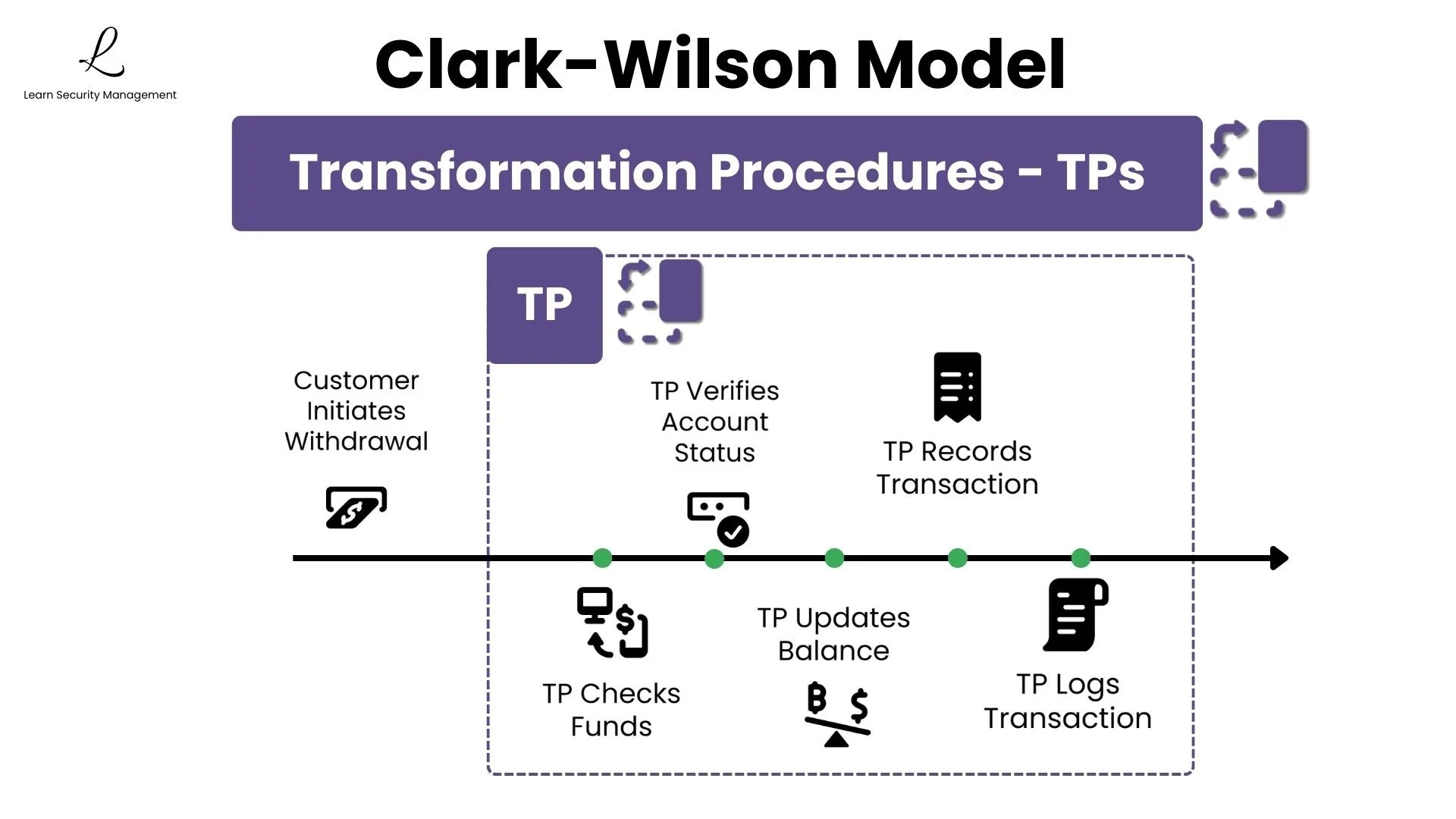
Think of a Transformation Procedure as a secure gateway. When a customer withdraws money from a bank account, the withdrawal must go through a TP that checks available funds, verifies account status, updates the balance, and logs the transaction. The TP contains all business logic, and if you try to bypass it, you're blocked entirely.
A key distinction for the exam: in Clark-Wilson, users never have direct access to data. All access is mediated through Transformation Procedures. This is fundamentally different from models like Biba, where users might have direct read or write access based on integrity levels.
Well-Formed Transactions
Having a procedure isn't enough. It must be proven to preserve data integrity. This is where well-formed transactions come in. A well-formed transaction ensures that data moves from one valid state to another valid state, with no possibility of leaving data in an inconsistent or corrupted condition.
Consider a funds transfer between two accounts. A well-formed transaction must debit one account and credit another as an atomic operation, meaning it is all or nothing. If the debit succeeds but the credit fails, the system rolls back the entire transaction. The money cannot simply vanish or appear from nowhere.
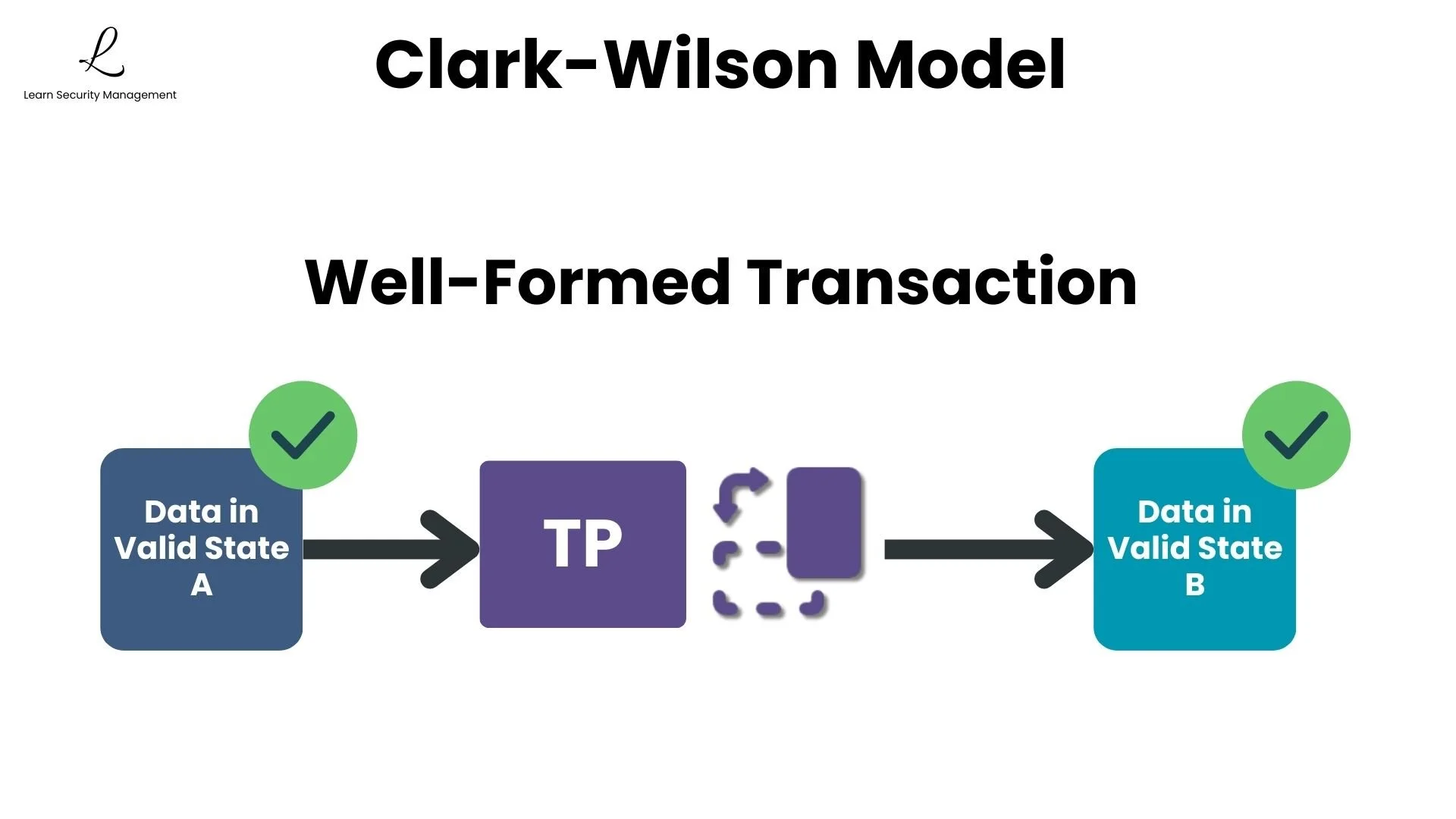
Well-formed transactions and certified Transformation Procedures reflect Clark-Wilson's Certification Property, the quality control mechanism that ensures procedures preserve integrity. Procedures must be tested, validated, and certified before deployment to guarantee they maintain valid data states.
Preventing Fraud Through Separation of Duties
Having certified procedures isn't enough on its own. Clark-Wilson implements its second core mechanism, Enforcement, through separation of duties. This principle ensures that no single person can compromise data integrity, even if they have legitimate access to certain transactions.
The Separation of Duties Principle
The principle is straightforward: different users must perform different transaction steps, and no single person should have complete control over a critical process. This prevents both intentional fraud and accidental corruption by requiring multiple people to be involved in sensitive operations.
This is where Clark-Wilson differs from purely technical models. It recognizes that authorized users pose the biggest integrity risk. A purchasing agent who can both order goods and approve payments could create fake vendors and steal money. The model requires different people to handle these steps, creating checks and balances within the organization.
Consider the classic accounts payable process. One person creates the purchase order, a different person receives the goods and creates a receiving report, and a third person matches the invoice to both documents before authorizing payment. This three-way match prevents a single employee from creating fraudulent purchases and payments.
Access Control Triplets
Clark-Wilson enforces separation of duties through a precise mechanism: access control triplets. Each triplet defines exactly which users can perform which actions on which data, creating a granular control system that prevents unauthorized or conflicting access.
The Three Components
Each access control triplet consists of three elements: a User (the person or role), a Transformation Procedure (the action they can perform), and a Constrained Data Item (the data they can access through that procedure). Without all three elements matching in an authorized triplet, access is denied.
| User/Role | Transformation Procedure | Constrained Data Item |
|---|---|---|
| Bank Teller | Process Withdrawal | Customer Accounts |
| Loan Officer | Approve Loan | Loan Applications |
| Auditor | Generate Report | Transaction Logs |
How Triplets Enforce Separation
In our banking example, a teller has an authorized triplet: (Teller, Process Withdrawal, Customer Accounts). This allows them to process withdrawals. However, the teller does not have a triplet for (Teller, Approve Loan, Loan Applications), so they cannot approve loans, even though they work for the same bank and might see loan application data.
A loan officer has a different triplet: (Loan Officer, Approve Loan, Loan Applications). But the loan officer cannot process withdrawals because they don't have that triplet. Each role's access is precisely defined by their specific authorized triplets, creating separation of duties that prevents any single employee from completing high-risk transactions alone.
Remember that access control triplets are unique to Clark-Wilson. When exam questions mention triplets consisting of (User, Program/Procedure, Data), the answer involves Clark-Wilson. This is distinctly different from the subject-object-access rights model used in other frameworks.
Implementation Requirements
Implementing Clark-Wilson requires significant organizational commitment. The model works best in environments where data accuracy is critical, but requires upfront investment to implement properly.
Five Implementation Steps
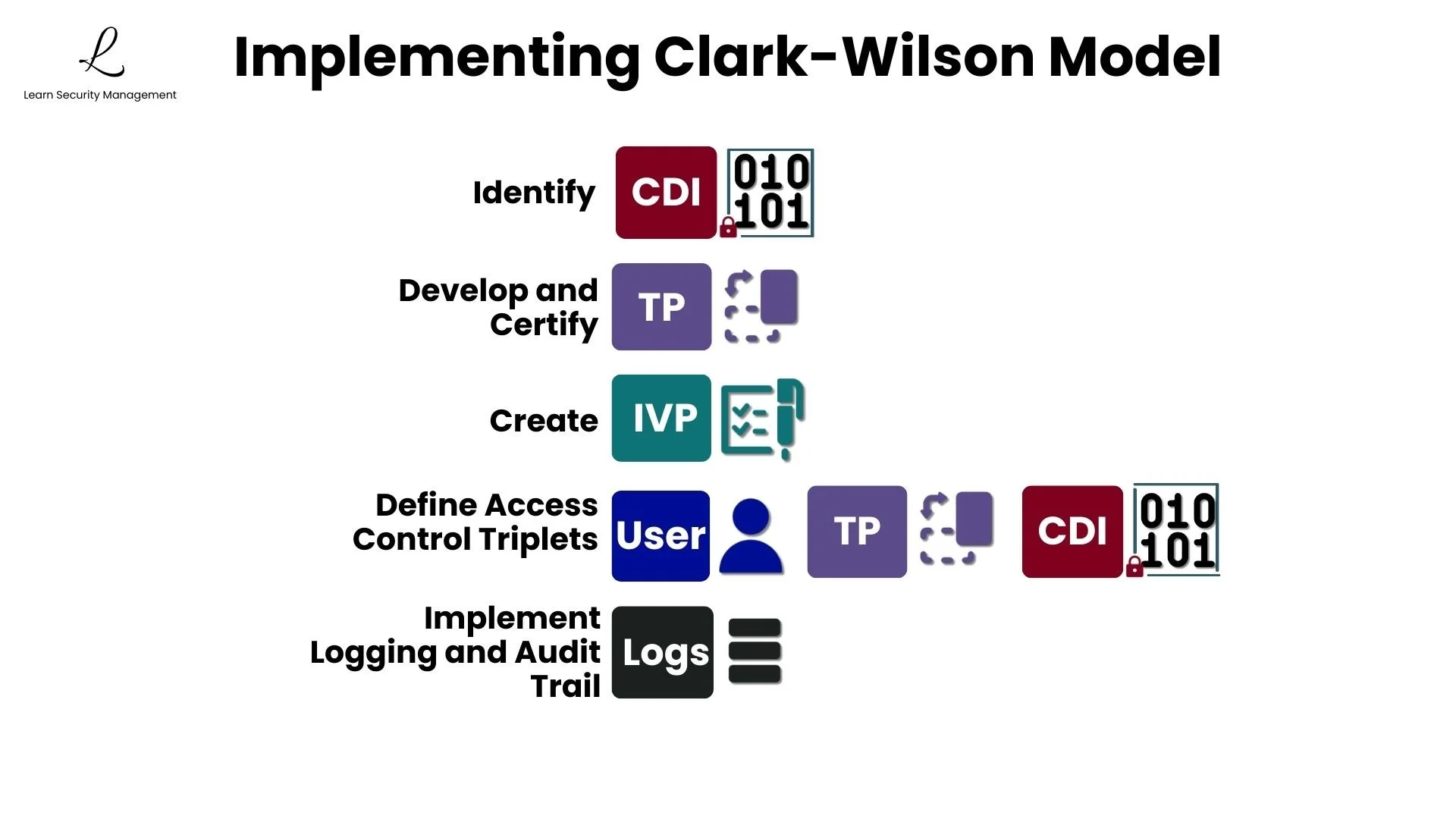
Organizations implementing Clark-Wilson must complete five key steps:
- Identify CDIs: Determine which data assets require integrity protection
- Develop and Certify TPs: Create transformation procedures with proven integrity preservation
- Create IVPs: Implement integrity verification procedures to validate data states
- Define Access Control Triplets: Specify which users can execute which procedures on which data
- Implement Logging and Audit Trails: Ensure all transactions are recorded for accountability
Clark-Wilson only addresses data integrity. It provides no inherent protection for confidentiality or availability. Organizations must combine this model with other access controls (like Bell-LaPadula for confidentiality) to achieve comprehensive security. Additionally, the model requires ongoing maintenance as business processes evolve.
The Clark-Wilson model addresses integrity goals in a commercial environment. It focuses on well-formed transactions and separation of duties to protect the integrity of data... Access is mediated through programs.
CISSP Official Study Guide, 9th Edition
Conclusion
The Clark-Wilson Model provides the gold standard for commercial data integrity by combining well-formed transactions with separation of duties. Through its classification of data into CDIs and UDIs, mediation of access through certified Transformation Procedures, and enforcement via access control triplets, the model addresses both accidental corruption and intentional fraud.
Understanding the distinction between Certification (ensuring procedures preserve integrity) and Enforcement (controlling who can execute procedures) is essential for CISSP candidates. The model's unique characteristics, including indirect access through TPs, access control triplets, and mandatory separation of duties, frequently appear in exam scenarios involving financial systems, inventory management, and commercial data processing.
For CISSP exam success, remember that Clark-Wilson is the answer when scenarios involve commercial integrity, preventing fraud through separation of duties, or requiring that users access data only through approved programs. When you see "well-formed transactions," "access control triplets," or "Transformation Procedures," think Clark-Wilson.
CISSP Practice Tests
Challenge yourself with tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the ChallengeThe Clark-Wilson Model is a security framework that protects commercial data integrity through well-formed transactions and separation of duties. It ensures users can only modify protected data through certified procedures, never directly.
Data Classification
- CDIs (Constrained Data Items): Protected data requiring integrity controls (financial records, inventory)
- UDIs (Unconstrained Data Items): Uncontrolled data that can be modified freely (uploads, drafts)
- IVPs (Integrity Verification Procedures): Automated checks validating CDI integrity
Access Control Mechanisms
- Transformation Procedures (TPs): Certified programs that mediate all access to CDIs
- Well-Formed Transactions: Operations that move data from one valid state to another
- Access Control Triplets: (User, TP, CDI) combinations defining authorized access
Two Core Properties
- Certification: Ensures procedures preserve data integrity (quality control)
- Enforcement: Controls who can execute which procedures (access control)
Key Characteristics
- Indirect Access: Users never access data directly, always through TPs
- Separation of Duties: No single user can complete critical transactions alone
- Commercial Focus: Designed for business environments where accuracy matters
Common Exam Scenarios
- Banking systems requiring transaction integrity
- Inventory management preventing fraud
- Financial systems with audit requirements
- Any scenario mentioning "well-formed transactions" or "triplets"
To instantly identify the correct model on the exam:
- If the threat is Unauthorized Disclosure (espionage, leaking secrets), the solution is Bell-LaPadula.
- If the threat is Data Corruption (sabotage, integrity labels), the solution is Biba.
- If the threat is Commercial Fraud (fraudulent transactions, business integrity), the solution is Clark-Wilson.
- If the threat is Conflict of Interest (competing clients, ethical walls), the solution is Brewer and Nash.
Managerial Takeaway: Bell-LaPadula hides secrets, Biba protects truth through labels, Clark-Wilson prevents fraud through procedures, Brewer and Nash prevents ethical violations.

