The Graham-Denning Model is a foundational access control framework that defines how systems create, manage, and control access to objects and subjects. Unlike confidentiality-focused models like Bell-LaPadula or integrity models like Biba, Graham-Denning addresses a different challenge: who has the authority to grant or revoke access rights in a secure system?
This model provides eight fundamental operations that govern access control in secure systems. It is especially valuable in distributed or multi-user environments where control over permissions is just as important as the permissions themselves. For CISSP candidates, understanding Graham-Denning is essential for the Security Architecture and Engineering domain, particularly when analyzing how access control decisions are made and delegated.
Watch the complete video guide on the Graham-Denning Model
What is the Graham-Denning Model?
The Graham-Denning Model is a formal security model that specifies how access control should be managed in a secure computing environment. While other models define what access is permitted (like Bell-LaPadula's confidentiality rules or Biba's integrity rules), Graham-Denning defines how access rights are created, modified, transferred, and revoked.
Think of it this way: Bell-LaPadula tells you that a Secret-cleared user cannot read Top Secret documents. But who decides that a user gets Secret clearance in the first place? Who can grant them access to specific documents? Who can take that access away? These are the questions Graham-Denning answers.
Bell-LaPadula: Defines what you can read and write (confidentiality rules)
Biba: Defines what you can read and write (integrity rules)
Graham-Denning: Defines who can create, manage, and transfer access rights
The model is particularly important in environments where access control decisions are distributed—cloud systems, enterprise networks, and multi-tenant platforms. In these environments, you need formal rules for how administrators create user accounts, how managers delegate permissions to their teams, and how ownership of resources transfers when employees change roles.
Subjects and Objects
Graham-Denning operates on three core components that form the foundation of all access control decisions. Understanding these components is essential before exploring the eight operations.
Subjects: The Active Entities
A subject is any active entity that can perform actions in the system. This includes users logged into their accounts, running applications, and background processes. Subjects are the actors that initiate operations and request access to resources.
Objects: The Passive Resources
An object is any passive resource that subjects interact with. This includes files, databases, printers, network resources, and even other subjects when they are being acted upon. Objects are the targets of access requests.
When you open a document, you're the subject and the document is the object. When a backup process copies files to storage, the process is the subject and the files are objects. The same entity can be both a subject and an object depending on context—a user account is an object when being created by an administrator, but becomes a subject when that user logs in and accesses files.
Access Rights: The Permissions
Access rights define what a specific subject can do with a specific object—read it, modify it, delete it, or control who else can access it. These rights are stored in an access control matrix that maps subjects to objects and specifies their permissions.
Graham-Denning uses an access control matrix to track all relationships between subjects and objects. Each cell in the matrix contains the access rights that a specific subject holds over a specific object. The eight operations defined by the model are the only ways to modify this matrix.
The Eight Operations
Graham-Denning defines exactly eight operations that govern how subjects, objects, and access rights are managed. These operations fall into two categories: entity operations that manage the lifecycle of subjects and objects, and access right operations that control permissions.
Entity Operations (1-4)
The first four operations handle entity lifecycles—creating and deleting the subjects and objects that exist in the system.
| Operation | Description | Example |
|---|---|---|
| Create Object | Establish a new object in the system | Creating a new file, database, or folder |
| Delete Object | Remove an object from the system | Deleting a file or decommissioning a resource |
| Create Subject | Establish a new subject in the system | Creating a user account or starting a process |
| Delete Subject | Remove a subject from the system | Terminating a user account or ending a process |

Access Right Operations (5-8)
The remaining four operations manage the permissions themselves—how rights are examined, granted, revoked, and delegated.
| Operation | Description | Example |
|---|---|---|
| Read Access Right | Check a subject's current rights over an object | Auditing who has access to a file |
| Grant Access Right | Give a right to another subject | Sharing a document with a colleague |
| Delete Access Right | Remove a right from another subject | Revoking a former employee's access |
| Transfer Access Right | Pass a right to another subject | Delegating authority to a deputy |
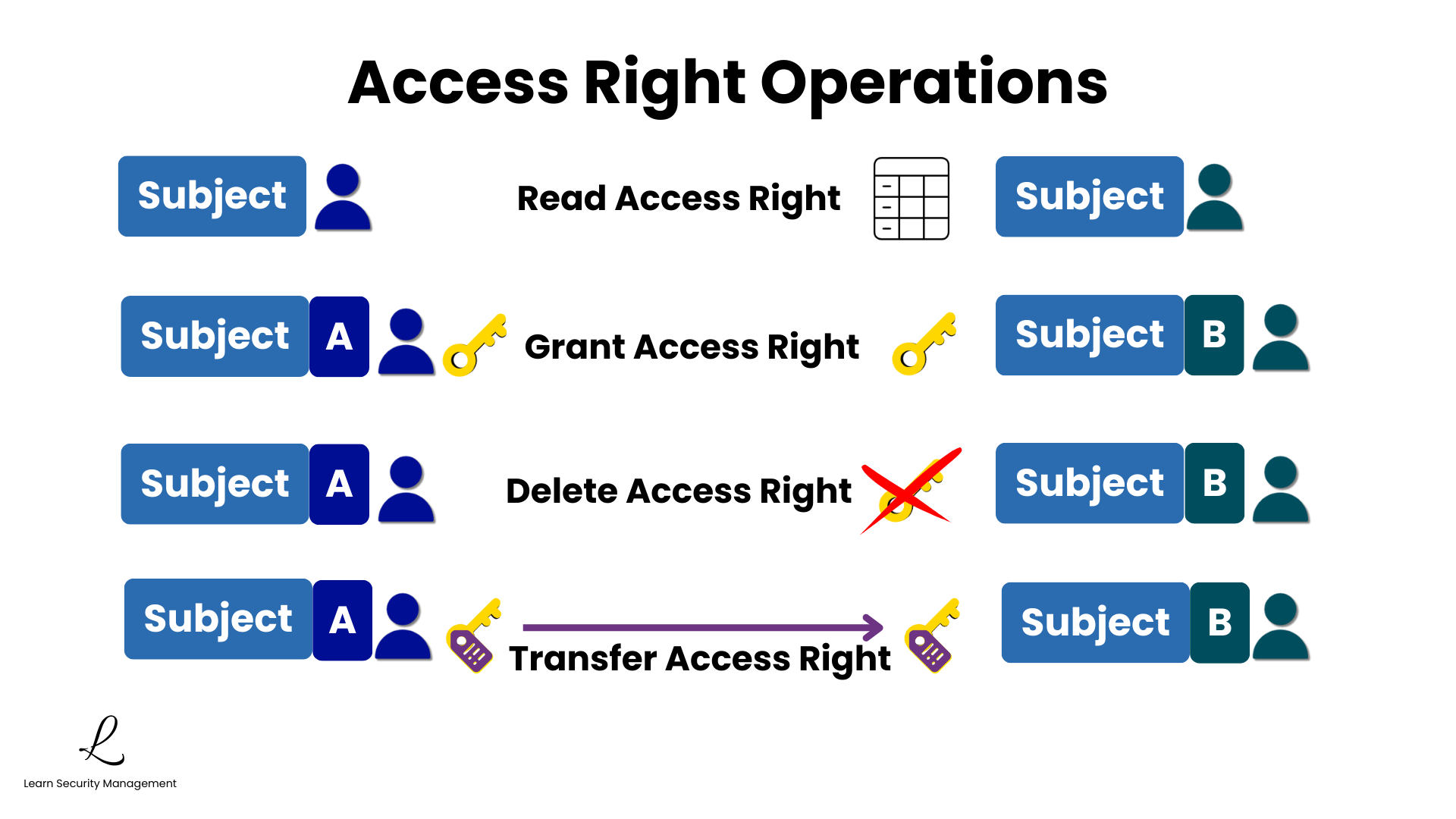
Pay attention to the distinction between Read Access Right and reading an object's content. Reading access rights means checking the permissions table to see who has what access—not reading the actual content of files. This is an administrative operation, not a data access operation.
Operations in Action: A Cloud Example
Consider how these operations work together in a real-world scenario. A cloud administrator creates a secure storage container for financial records—that's Create Object. They grant the automated billing service access using Grant Access Right.
When a security auditor verifies compliance, they check the access control lists to see who's authorized—that's Read Access Right. If the billing service is replaced, the administrator revokes the old service's permissions with Delete Access Right.
When the administrator goes on leave, they use Transfer Access Right to delegate access management authority to a senior analyst. The eight operations provide a complete framework for managing the entire lifecycle of subjects, objects, and their access relationships.
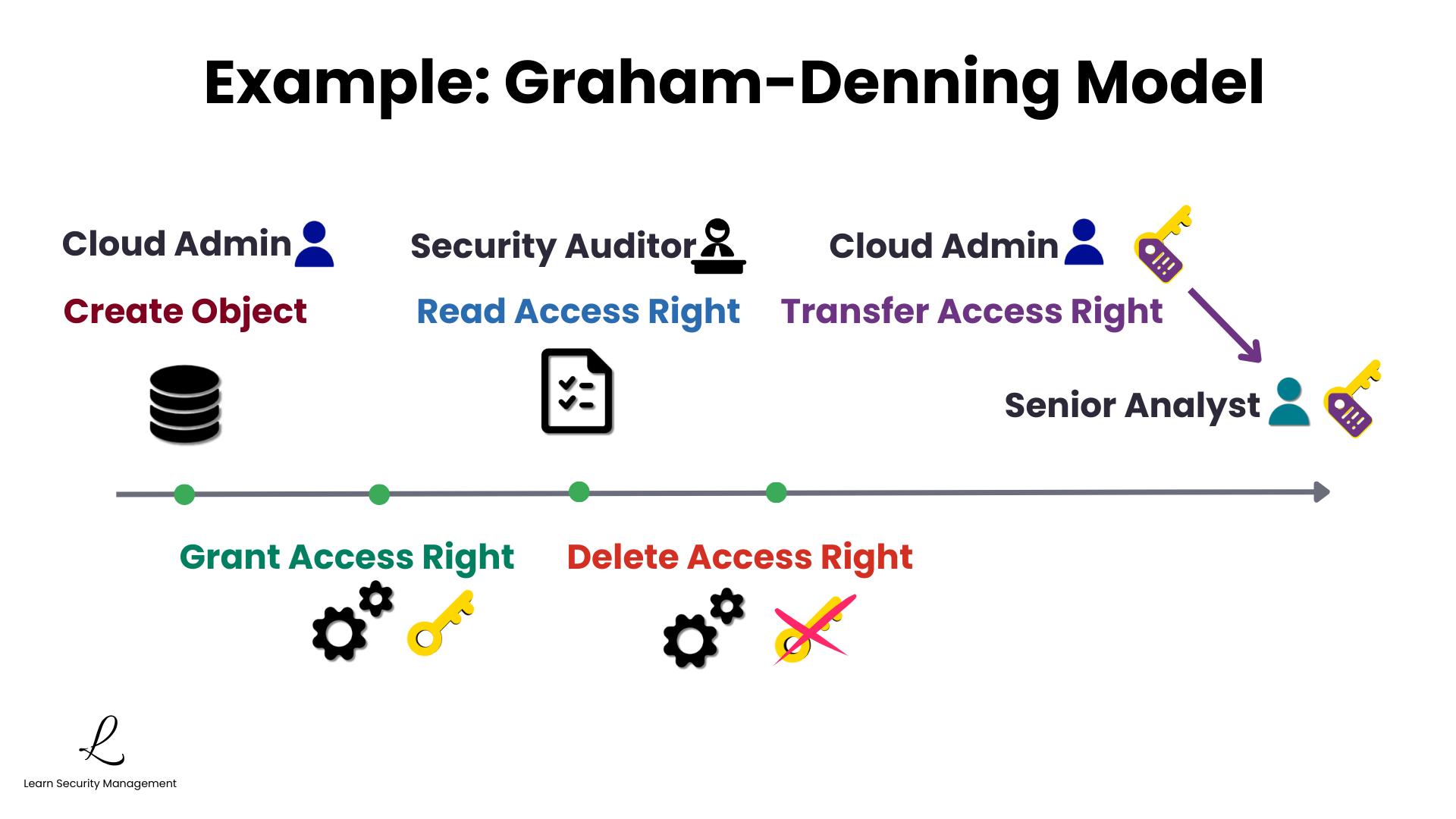
Control Rights and Ownership
The Graham-Denning Model introduces specific control rights that determine who can perform the eight operations. Understanding ownership and the transfer attribute is critical to how the model works in practice.
Ownership: The Foundation of Control
When you create an object, you become its owner with full control rights. As owner, you can grant others access and specify whether they can pass those rights further. Ownership is the root of all access control authority in the Graham-Denning Model.
The owner of an object has complete authority over it. They can grant access to others, revoke access from others, and even transfer ownership itself. This creates a clear chain of authority that can be traced back to whoever created the resource.
The Transfer Attribute
A right can be granted with or without a transfer attribute. If a right is granted with the transfer attribute, the receiving subject can then pass that same right on to others. This creates a hierarchy of authority and enables delegation throughout the system.
It's important to note that transfer does not mean permanent delegation—the original owner retains ultimate control and can revoke any rights at any time. The transfer attribute simply enables controlled delegation while maintaining accountability.
A legal director creates a contracts repository and becomes its owner. They grant junior staff read access without transfer—staff can view contracts but can't share access with others. They grant senior lawyers read access with transfer, so they can bring in external consultants as needed. The director maintains ultimate control while enabling appropriate delegation.
Rights With and Without Transfer
| Right Type | Recipient Can... | Use Case |
|---|---|---|
| Without Transfer | Use the right, but cannot delegate it to others | Standard employee access to resources |
| With Transfer | Use the right AND pass it to other subjects | Manager delegation to team leads |
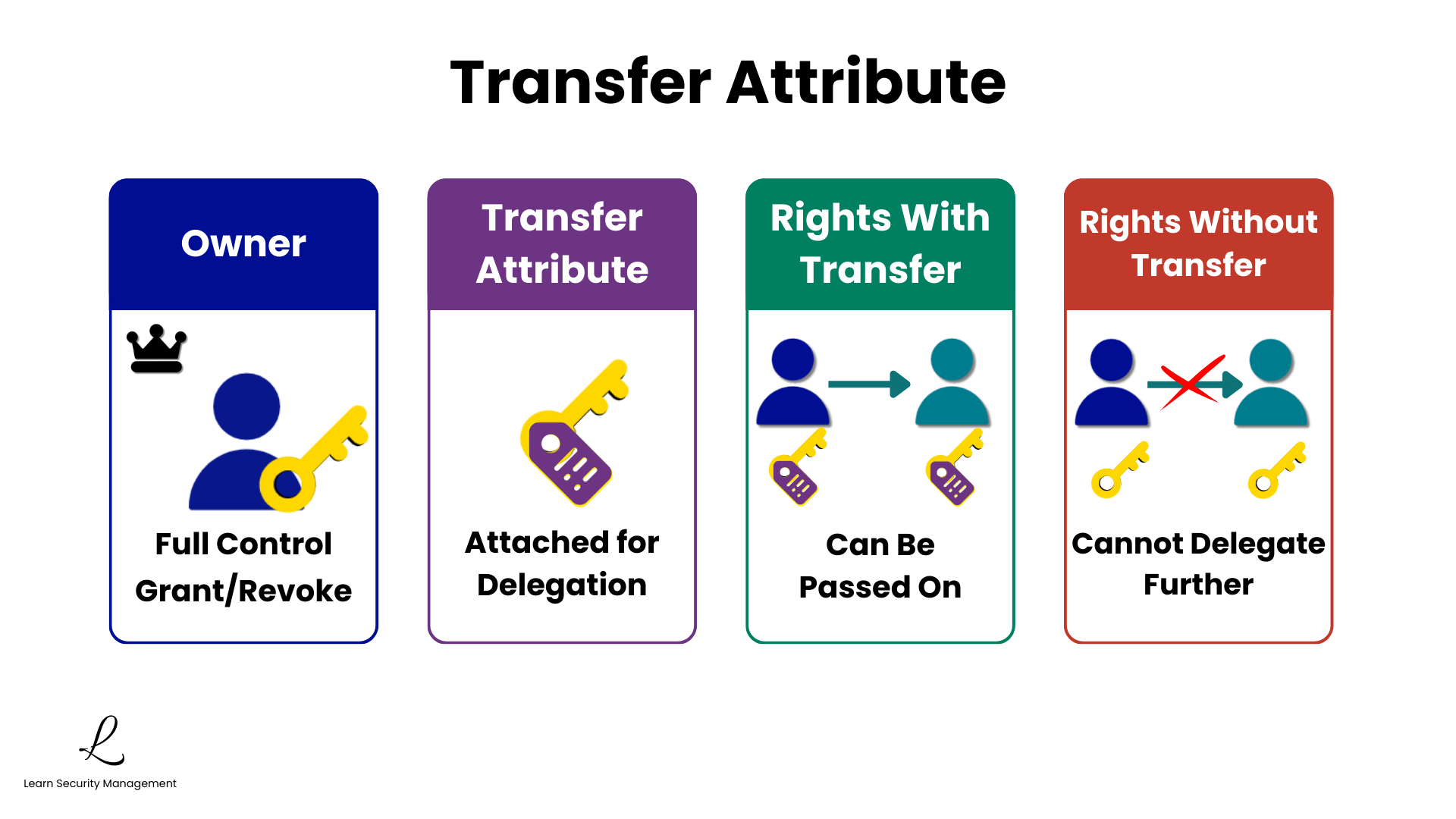
Remember that the transfer attribute creates a delegation chain, but the original owner always retains the ability to revoke any rights—including rights that have been transferred multiple times. Ownership trumps delegation.
Practical Applications
Understanding where Graham-Denning applies helps contextualize its importance. The model is particularly relevant in modern distributed computing environments.
Enterprise Access Management
In enterprise environments, Graham-Denning principles appear in identity and access management (IAM) systems. When an HR administrator creates a new employee account (Create Subject), grants them access to departmental resources (Grant Access Right), and later revokes that access upon termination (Delete Access Right), they're following Graham-Denning operations.
Cloud and Multi-Tenant Systems
Cloud platforms implement Graham-Denning concepts when managing permissions across tenants. Each tenant can create resources (Create Object), share them with other users (Grant Access Right), and audit who has access (Read Access Right). The platform ensures that tenants can only manage permissions for their own resources.
Comparison with Other Models
| Model | Primary Focus | Addresses |
|---|---|---|
| Bell-LaPadula | Confidentiality | What can be read/written based on clearance |
| Biba | Integrity | What can be read/written based on trust |
| Clark-Wilson | Commercial Integrity | Well-formed transactions and separation of duties |
| Graham-Denning | Access Control Management | Who can create, modify, and transfer access rights |
Graham-Denning doesn't compete with other security models—it complements them. You might use Bell-LaPadula to define confidentiality rules and Graham-Denning to specify how those rules are established and managed. The models address different aspects of a complete security architecture.
Security models provide formal frameworks for specific security properties. Graham-Denning is unique in focusing on the administrative aspects of access control—how rights are created and managed rather than what access should be permitted.
CISSP Official Study Guide, 9th Edition
Conclusion
The Graham-Denning Model provides a formal framework for managing access control in secure systems. By defining eight fundamental operations—four for entity management and four for access right management—the model establishes clear rules for how subjects, objects, and permissions are created, modified, and revoked.
Understanding the distinction between ownership and delegated rights, and between rights with and without transfer attributes, is essential for implementing secure access control systems. These concepts appear throughout modern IAM platforms, cloud services, and enterprise security architectures.
For CISSP exam success, focus on understanding the eight operations and their practical applications. Remember that Graham-Denning addresses access control management—who can grant and revoke permissions—rather than the access rules themselves. When exam scenarios involve creating accounts, delegating authority, or auditing permissions, the Graham-Denning Model is your answer.
CISSP Practice Tests
Challenge yourself with tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the ChallengeThe Graham-Denning Model is a security framework that defines how access control is managed in secure systems. It specifies eight fundamental operations for creating, managing, and controlling access to objects and subjects.
Core Components
- Subjects: Active entities that perform actions (users, processes, applications)
- Objects: Passive resources that are accessed (files, databases, printers)
- Access Rights: Permissions that subjects hold over objects
The Eight Operations
- Create Object: Establish a new object in the system
- Delete Object: Remove an object from the system
- Create Subject: Establish a new subject in the system
- Delete Subject: Remove a subject from the system
- Read Access Right: Check a subject's current rights over an object
- Grant Access Right: Give a right to another subject
- Delete Access Right: Remove a right from another subject
- Transfer Access Right: Pass a right to another subject
Control Rights
- Owner: Full control over an object including granting and revoking access
- Transfer Attribute: Can be attached to any right to enable delegation
- Rights With Transfer: Receiving subject can pass the right to others
- Rights Without Transfer: Receiving subject cannot delegate further
Common Exam Mistakes
- Confusing Read Access Right with reading object content (it's checking permissions, not data)
- Assuming transfer means permanent delegation (owner retains ultimate control)
- Mixing up Graham-Denning with confidentiality or integrity models
- Forgetting that ownership originates from creation of an object
In Domain 3, the CISSP exam tests your ability to categorize models. While Bell-LaPadula and Biba are Static/Rule-Based models (they don't care how you got the permission, only that you have it), Graham-Denning is a Dynamic/State-Transition model.
1. The "Meta-Access" Trigger
If a question asks about "Access to Access," it is almost always Graham-Denning.
- Scenario A: "A user is blocked from reading a file." → This is a Bell-LaPadula or Biba issue.
- Scenario B: "A user is blocked from granting a colleague the ability to read a file." → This is a Graham-Denning issue.
2. The "Transfer" vs. "Grant" Nuance
The exam may try to trick you with these two:
- Grant Access: Subject A gives Subject B a right. (Think: Sharing a Google Doc).
- Transfer Access: Subject A gives Subject B a right plus the ability for Subject B to give it to Subject C. (Think: Adding an Editor who can also add other Editors).
Keywords to watch for: "Delegated Authority," "Propagation of Rights," or "Transitive Trust."
3. Practical "Manager" Takeaway
As a security manager, you use Graham-Denning concepts when designing Provisioning and Deprovisioning workflows:
- Creation/Deletion operations map to your Joiner/Mover/Leaver (JML) process.
- Grant/Transfer operations map to your Access Request/Approval workflow.
| Look for these Keywords | Think: Graham-Denning? |
|---|---|
| "Authority to delegate" | YES |
| "Creation/Deletion of Subjects" | YES |
| "No Read Up / No Write Down" | NO (Bell-LaPadula) |
| "State Transition of Permissions" | YES |
| "Access Control Matrix modification" | YES |
Bottom Line: Other models define what access is allowed. Graham-Denning defines who has the authority to grant or change that access.

