The Brewer and Nash Model, also known as the Chinese Wall Model, is a security framework designed to prevent conflicts of interest in environments where access to competing organizations' data could create ethical or legal problems. Unlike models that focus on confidentiality or integrity, this model dynamically restricts access based on a user's access history to ensure information from direct competitors never ends up in the same hands.
This model is particularly critical in consulting, legal, and financial services where professionals routinely work with multiple clients in the same industry. Understanding how the Brewer and Nash Model prevents information leakage between competitors is essential for CISSP candidates, especially when exam scenarios involve professional services, investment banking, or any environment requiring ethical walls between competing interests.
Watch the complete explanation of the Brewer and Nash Model with practical examples and CISSP exam tips.
What is the Brewer and Nash Model?
The Brewer and Nash Model is a security framework with one primary goal: ensuring that users who access information from one company cannot access sensitive data from its direct competitors. The model creates dynamic barriers—invisible walls—that form based on access decisions, preventing the same person from holding confidential information about competing organizations.
Core Purpose: Conflict of Interest Prevention
While Bell-LaPadula protects confidentiality and Biba protects integrity, the Brewer and Nash Model addresses a unique security concern: preventing competitive intelligence from crossing ethical boundaries. In professional services environments, having access to one company's strategic plans while also viewing a competitor's financial data creates an inherent conflict that could lead to insider trading, unfair business practices, or breach of fiduciary duty.
Unlike traditional models that assign fixed clearance levels, the Brewer and Nash Model creates access restrictions dynamically based on user behavior. Your access permissions change over time depending on which companies' data you have previously accessed. This history-dependent approach is what makes the model unique among access control frameworks.
The model is sometimes called the "Chinese Wall" because once you access one company's data, an invisible wall goes up between you and their competitors—just like a physical barrier separating parties who should not communicate or share information.
How Conflict of Interest Develops
Before understanding how the model works, it's essential to grasp the problem it solves. Conflicts of interest arise when one person has access to confidential information from multiple competing entities, creating opportunities for that information to influence decisions inappropriately.
The Core Problem
Imagine a financial analyst at a consulting firm. They review confidential financial data from Company A, a major smartphone manufacturer. If they can then access similar data from Company B, a competing smartphone manufacturer, they could use insights from one to benefit the other, create unfair advantages, or leak competitive intelligence. This creates a conflict of interest that could violate professional ethics, securities laws, or contractual obligations.
The Brewer and Nash Model is frequently tested in scenarios involving consulting firms, law practices, investment banks, and auditing companies—any environment where professionals serve multiple clients in the same industry. Look for keywords like "competitor," "conflict of interest," or "ethical wall" to identify when this model applies.
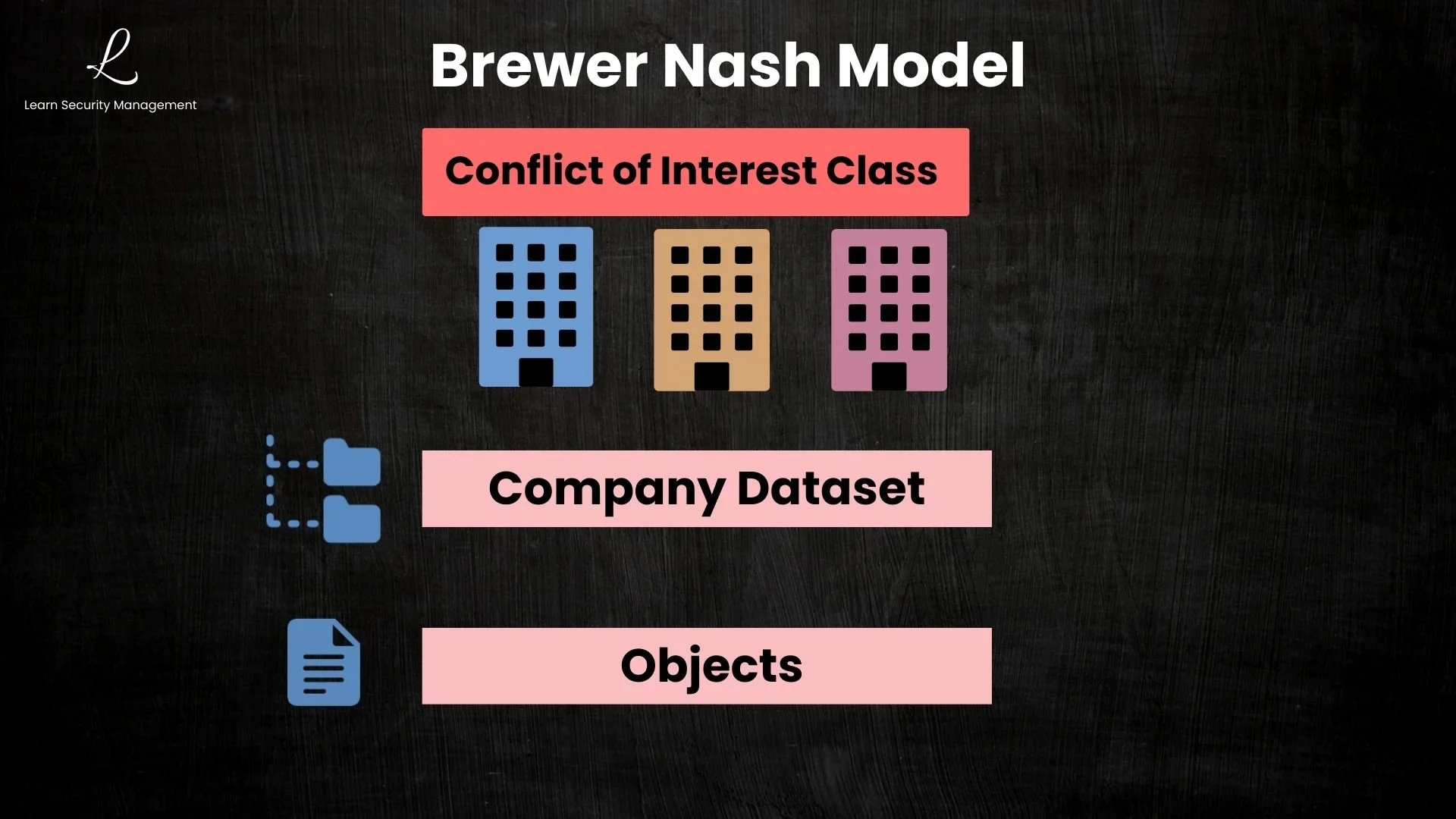
Three-Level Information Organization
The model organizes information into three hierarchical levels that determine how access restrictions are applied:
| Level | Description | Examples |
|---|---|---|
| Objects | Individual files or data items | Financial reports, strategy documents, contracts |
| Company Datasets | All data belonging to one organization | All of Company A's files grouped together |
| Conflict of Interest Classes | Groups of competing companies in the same industry | All smartphone manufacturers, all major banks |

At the bottom level, objects are individual files or data items like financial reports and strategy documents. These objects belong to company datasets, which contain all data from one specific organization. Finally, company datasets are grouped into conflict of interest classes, which bring together all competing companies in the same industry. Once you access data from one company in a class, you're blocked from all competitors in that same class.
A conflict of interest class groups companies that compete directly with each other. For example, a "Smartphone Manufacturers" class might include Apple, Samsung, and Google. A "Major Airlines" class might include United, Delta, and American. Companies in different classes (like a smartphone maker and an airline) don't conflict—a consultant could work with both without ethical issues.
The Chinese Wall Rule
The Brewer and Nash Model enforces its protection through one dynamic rule that adapts based on your access history. This is called the Chinese Wall Rule because once you access one company's data, an invisible wall goes up between you and their competitors.
The Access Control Rule
A user can access an object only if that object belongs to the same company dataset they've already accessed, OR if the object belongs to a completely different conflict of interest class that they haven't accessed yet.
- First Access is Unrestricted: Your first access in any conflict class is completely free—you can choose any company you want
- Competitors Become Blocked: After accessing one company's data, all competitors in that class are permanently blocked
- Other Classes Remain Open: You can still access companies in different conflict classes you haven't touched yet
- Wall Grows Dynamically: The wall builds over time, creating a unique access pattern based on your choices

The key insight is that restrictions are user-specific and history-dependent. Another consultant at the same firm might have accessed Company B instead of Company A, creating a completely different wall. The model doesn't use static clearance levels—your access history determines what you can and cannot see, and once you cross into a company's dataset, that decision is irreversible for that conflict class.
The Write Restriction (Preventing Leakage)
Most CISSP candidates focus solely on the read restriction, but the Brewer and Nash Model includes a critical write rule to prevent indirect information leakage. This rule is similar to the *-property in other models but adapted for conflicts of interest.
A subject can write information to an object only if they cannot read any object contained in a different company dataset.
This rule ensures that a consultant cannot read confidential secrets from "Company A" and then—accidentally or maliciously—write those secrets into a report or file accessible to "Company B." Without this restriction, the "wall" could be bypassed by simply copying data from one side to the other.
- Read Rule: You can read data if it doesn't conflict with your past access history.
- Write Rule: You cannot write to a dataset if you have read access to any other company's dataset (this prevents cross-contamination).
Consider an investment bank advising on mergers and acquisitions. An analyst working on Company A's acquisition strategy cannot then advise Company B, a direct competitor, on their defensive measures. The Chinese Wall ensures that confidential strategic information cannot flow between competing interests through the same person, protecting both clients and maintaining market integrity.
Practical Example: A Day in the Life
Let's see how these rules work in practice through a detailed scenario involving a consultant at a multi-industry advisory firm.
Morning: Automotive Industry Work
A consultant opens files from Company A, an automotive manufacturer. The system records that they've accessed the automotive conflict class through Company A. At this moment, they're permanently blocked from Company B and Company C, Company A's direct competitors in the automotive conflict class. They can continue accessing any of Company A's files, but the competing automotive manufacturers are now off-limits forever.
Afternoon: Telecommunications Project
Later that day, the consultant needs to work on a telecommunications project. Since they haven't accessed the telecommunications conflict class yet, they can freely choose to work with Company X, a major telecom provider. Once they open Company X files, they're blocked from Company Y and Company Z, Company X's competitors. The wall now exists in two industries for this consultant.

The Result
After these access decisions, the consultant can work with Company A (automotive) and Company X (telecommunications), but all competitors in both classes are permanently blocked. If another consultant at the same firm had made different initial choices—say, Company B in automotive and Company Y in telecommunications—they would have a completely different set of access permissions.
Remember that the Brewer and Nash Model is fundamentally about history-dependent, dynamic access control. Unlike Bell-LaPadula or Biba, which assign static clearance or integrity levels, this model's restrictions change based on user behavior. Questions often test whether you understand that access decisions are irreversible and that different users can have completely different access patterns.
Practical Limitations
While the Brewer and Nash Model effectively prevents conflicts of interest, it has significant challenges when implemented in real-world environments.
Progressive Access Restriction
As users access more companies across different industries, they build more walls and progressively lose access to more competitors. This can severely restrict user access over time. Eventually, a long-term employee might be blocked from large portions of the organization's client base simply because of the clients they've worked with historically.
| Limitation | Impact | Mitigation |
|---|---|---|
| Cumulative Restrictions | Users lose access over time | Strategic assignment planning |
| Staffing Complexity | May require multiple users for coverage | Maintain pool of "clean" consultants |
| Irreversible Decisions | No mechanism to reset walls | New user accounts (loses institutional knowledge) |
| Single Focus | Only addresses conflict of interest | Combine with other security models |
Operational Complexity
Organizations may need multiple users to cover all clients because individual consultants become restricted over time. They must carefully plan which consultants work with which clients, considering both immediate needs and long-term strategic implications. Once assigned, those decisions are permanent—there's no mechanism to reset or modify historical walls without creating a new user account, which means losing institutional knowledge and continuity.
The Brewer and Nash Model only addresses conflict of interest prevention. It provides no protection for confidentiality (information could still be disclosed to unauthorized parties who don't have conflicting access), integrity (data could still be modified), or availability. Organizations must combine this model with other access controls and monitoring systems to address these gaps.
No Security Level Hierarchy
Unlike Bell-LaPadula or Biba, the Brewer and Nash Model doesn't establish any hierarchy of sensitivity or trust. All companies within a conflict class are treated equally—there's no concept of one company's data being more confidential or trustworthy than another's. This means organizations need additional controls if they want to implement different access requirements for different types of information within each company's dataset.
The Chinese Wall model is designed specifically to prevent conflicts of interest, not to provide general-purpose access control. Its dynamic, history-based approach is powerful for its intended purpose but must be supplemented with other controls for comprehensive security.
CISSP Official Study Guide, 9th Edition
Conclusion
The Brewer and Nash Model provides a unique approach to access control by dynamically building restrictions based on user behavior rather than static clearance levels. Through its conflict of interest classes and the Chinese Wall Rule, it ensures that professionals working with multiple clients cannot access competing organizations' sensitive information.
Understanding the three-level information hierarchy—objects, company datasets, and conflict of interest classes—is essential for CISSP candidates. The model's key characteristic is that access decisions are irreversible and user-specific: once you access one company's data, their competitors are permanently blocked for you, even though another user might have completely different restrictions.
For CISSP exam success, remember that the Brewer and Nash Model addresses a specific problem—conflicts of interest—and provides no protection for confidentiality, integrity, or availability. When exam scenarios involve consulting firms, law practices, investment banks, or any environment with competing clients in the same industry, the Brewer and Nash (Chinese Wall) Model is your answer.
CISSP Practice Tests
Challenge yourself with tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the ChallengeThe Brewer and Nash Model (Chinese Wall Model) is a security framework that prevents conflicts of interest by dynamically restricting access based on user history. It ensures users who access one company's data cannot access data from direct competitors.
Three-Level Information Hierarchy
- Objects: Individual files or data items (financial reports, strategy documents)
- Company Datasets: All data belonging to one organization
- Conflict of Interest Classes: Groups of competing companies in the same industry
The Chinese Wall Rule
- First Access: Unrestricted choice within any conflict class
- After Access: All competitors in that class become permanently blocked
- Other Classes: Remain accessible until you make a choice in each
- Irreversible: Access decisions cannot be undone
Key Characteristics
- Dynamic Access Control: Restrictions change based on user behavior, not static clearance levels
- User-Specific: Each user builds their own unique wall based on their access history
- History-Dependent: Past access decisions determine future permissions
Practical Limitations
- Progressive Restriction: Users lose access over time as they work with more clients
- No Reset Mechanism: Cannot undo access history without creating new accounts
- Single Focus: Only addresses conflicts of interest—no confidentiality, integrity, or availability protection
Common Exam Scenarios
- Consulting firms working with multiple clients in the same industry
- Law firms representing competing companies
- Investment banks advising on mergers and acquisitions
- Auditing firms with clients who are competitors
To instantly identify the correct model on the exam:
- If the threat is Unauthorized Disclosure (espionage, leaking secrets), the solution is Bell-LaPadula.
- If the threat is Data Corruption (sabotage, integrity violations), the solution is Biba.
- If the threat is Conflict of Interest (competing clients, ethical walls), the solution is Brewer and Nash.
Managerial Takeaway: Bell-LaPadula hides secrets, Biba protects truth, Brewer and Nash prevents ethical violations.

