Kerberos is the primary network authentication protocol securing over 90% of enterprise environments, including all Microsoft Active Directory domains and most Unix/Linux networks. Understanding how this ticket-based system enables single sign-on while preventing password transmission is essential for CISSP candidates, particularly in the Identity and Access Management domain.
Named after Cerberus, the three-headed dog from Greek mythology that guards the underworld, Kerberos uses symmetric key cryptography to verify user and service identities across unsecured networks. Developed at MIT in the 1980s, it has become the de facto standard for enterprise authentication, providing mutual authentication, replay attack prevention, and seamless single sign-on capabilities.
Watch the complete Kerberos authentication flow with visual explanations of each step, from initial login to service access.
What is Kerberos?
A network authentication protocol is a set of rules and procedures that allows systems to verify the identity of users and services across a network before granting access to resources. Kerberos uses a ticket-based system to enable single sign-on access to multiple services without transmitting passwords across the network.
Core Definition and Purpose
Kerberos provides a centralized authentication service that eliminates the need to send passwords over potentially insecure networks. Instead of authenticating to each service individually, users prove their identity once to the Kerberos system and receive encrypted tickets that grant access to network resources.
The protocol operates within a Kerberos "realm" - a secure administrative boundary for authentication. Each realm manages its own users, services, and policies, and has its own Key Distribution Center (KDC). Realms are usually named in uppercase and often match an organization's domain name, such as LEARNSECURITYMANAGEMENT.COM. Large organizations can have multiple realms, and these realms can be linked so users from one can access services in another through cross-realm trust.
In Kerberos, every user, service, or host that participates in authentication is identified by a unique name called a principal. A principal typically has three parts: the primary (username or service name), an optional instance (admin role or hostname), and the realm. For example, a user might have the principal alice@LEARNSECURITYMANAGEMENT.COM, while a service could be host/appserver01.learnsecuritymanagement.com@LEARNSECURITYMANAGEMENT.COM.
Key Characteristics
Kerberos makes sure both the user and the service prove who they are to each other, so both sides know they're talking to the right person or system - this is called mutual authentication. Instead of sending your password every time you access something, Kerberos uses secret codes called tickets that are created using shared keys known only to you and the system.
This ticket system means you log in once and then use tickets to access different services, which is called single sign-on. Because passwords aren't sent over the network again and again, your information stays safer. Each ticket has a time limit, so old tickets can't be reused by attackers, which is why all computers using Kerberos need to have their clocks synchronized - typically within five minutes of each other.
Kerberos relies heavily on timestamps to prevent replay attacks. All systems in a Kerberos realm must maintain synchronized clocks, typically using Network Time Protocol (NTP). If a system's clock drifts too far (usually more than 5 minutes), authentication will fail. This time sensitivity is both a security feature and a potential availability concern.
The Three Components of Kerberos
Kerberos architecture consists of three main components that work together to provide secure authentication. Understanding how these components interact is crucial for CISSP candidates, as questions often focus on the flow of authentication requests and ticket issuance.
Authentication Server (AS)
The Authentication Server checks your username and password when you first log in. If your credentials are correct, it issues a Ticket Granting Ticket (TGT). The Authentication Server is the first checkpoint in Kerberos - it maintains the database of user accounts and ensures you are who you say you are.
Instead of sending your password over the network, the AS uses secure cryptographic methods to confirm your identity. When you attempt to log in, your workstation encrypts a timestamp using a key derived from your password and sends it to the AS. The AS decrypts this timestamp using the password hash it has stored. If successful, the AS knows you possess the correct password without the password ever being transmitted.
The Authentication Server never sees your actual password - it only sees encrypted data that can be decrypted using a key derived from your password. This design protects credentials even if network traffic is intercepted, as the encrypted timestamp is useless without the password to decrypt it.
Ticket Granting Server (TGS)
The Ticket Granting Server issues service tickets after verifying your TGT. When you want to use a service like a file server or database, you present your TGT to the TGS, and it gives you the specific ticket you need - no need to enter your password again.
Think of the TGS like a ticket booth at an amusement park. After you've shown your entrance ticket (the TGT), the TGS hands out tickets for each ride (service) you want to access. This way, you can access different services without typing your password each time. The TGS also controls which services you can use and for how long based on your permissions.
Key Distribution Center (KDC)
The Key Distribution Center typically combines both the Authentication Server and Ticket Granting Server in one system. While the AS and TGS are separate concepts, they're usually implemented together for convenience and efficiency. In Microsoft Active Directory, domain controllers act as KDCs and handle all authentication requests for the network.
The KDC stores all the security keys and secret passwords (in hashed form) for every user and service in the realm. Protecting the KDC is critical because compromise of this system means an attacker could potentially impersonate any user or service in the domain. Organizations typically deploy multiple domain controllers for redundancy, with each functioning as a KDC.
Exam questions often test your understanding of the difference between the AS and TGS functions, even though they're typically combined in the KDC. Remember: AS issues TGTs after initial authentication, while TGS issues service tickets for accessing specific resources. The KDC is the physical implementation that houses both services.
| Component | Primary Function | Key Security Role |
|---|---|---|
| Authentication Server (AS) | Verifies user credentials during initial login | Issues Ticket Granting Tickets (TGT) after successful authentication |
| Ticket Granting Server (TGS) | Validates TGTs and issues service tickets | Controls access to specific network services based on permissions |
| Key Distribution Center (KDC) | Houses both AS and TGS in single system | Stores all encryption keys and manages authentication infrastructure |
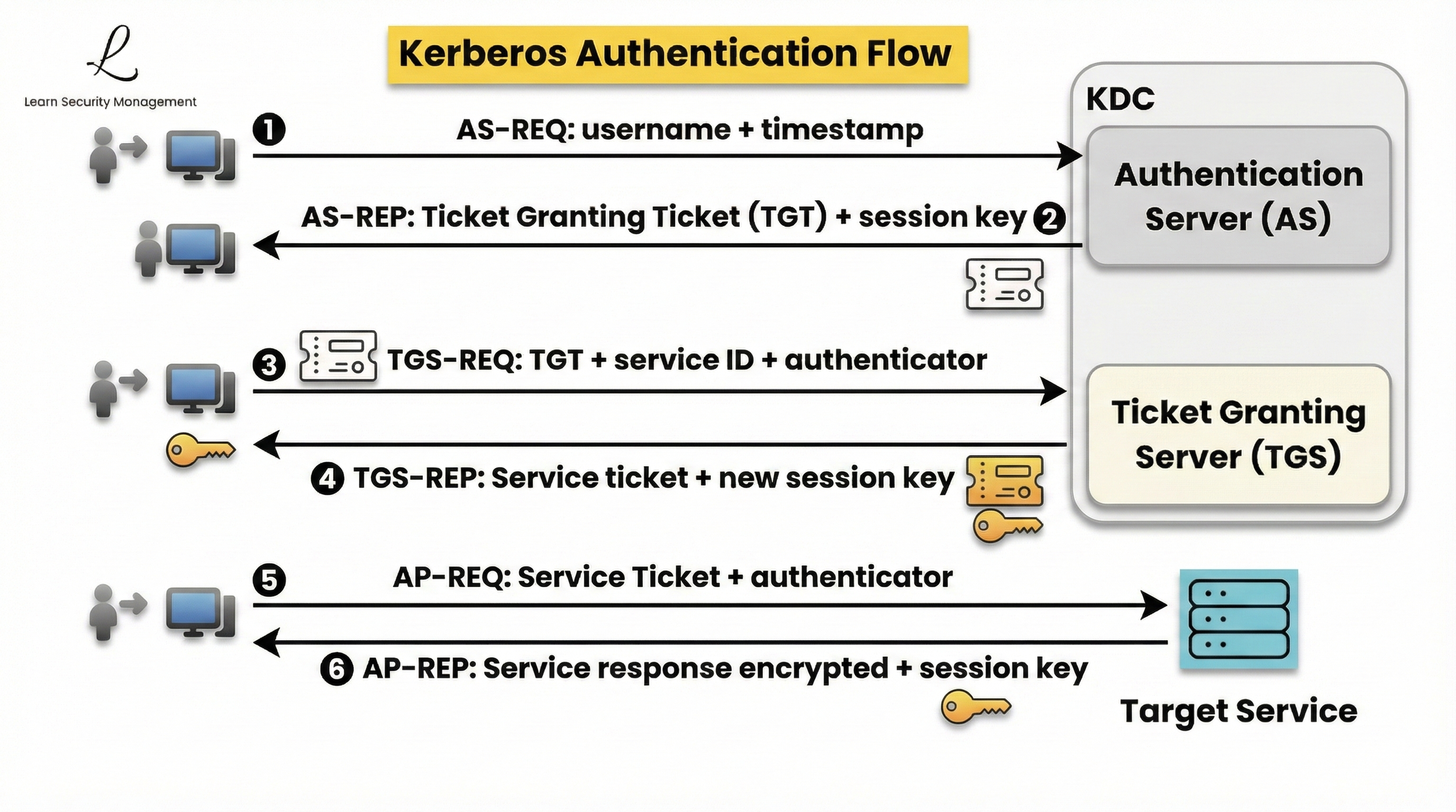
How Kerberos Authentication Works
The main goal of the Kerberos authentication process is to let a user securely access a service on the network - such as a file server, database, or web application - without sending their password each time. Understanding this six-step process is essential for CISSP candidates, as exam questions frequently test the sequence and purpose of each step.
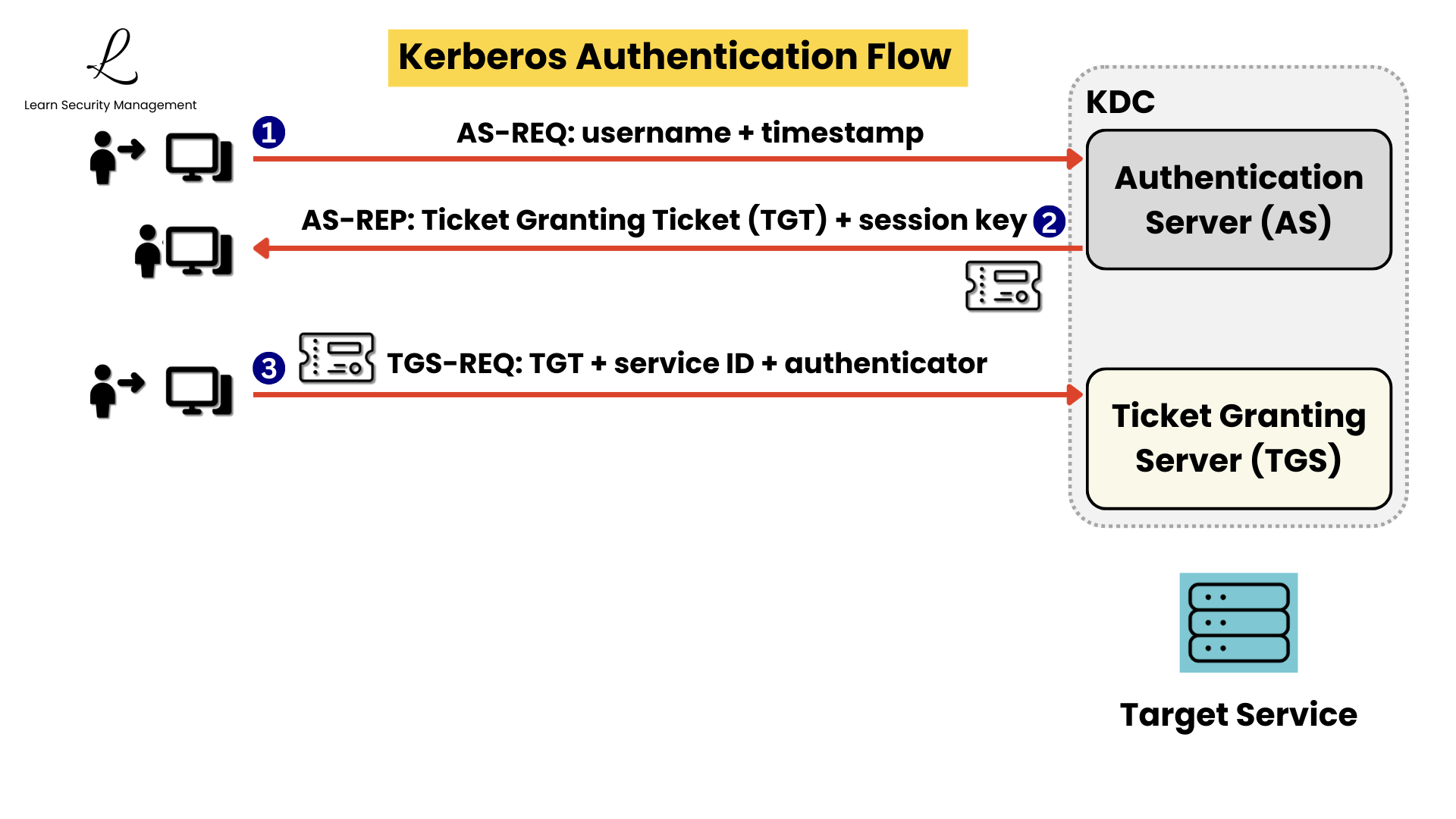
Step 1: Initial Authentication Request (AS-REQ)
When a user attempts to log in, their workstation sends an Authentication Server Request to the AS in the KDC. This request includes the username and a timestamp encrypted with a key derived from the user's password. The timestamp serves a critical security function - it prevents replay attacks by ensuring the request is current and hasn't been captured and retransmitted by an attacker.
At this stage, the actual password never crosses the network. Instead, the client proves knowledge of the password by successfully encrypting the timestamp using a key that can only be derived from the correct password. This cryptographic proof of password knowledge is what makes Kerberos secure even on untrusted networks.

Step 2: TGT Issuance (AS-REP)
If the Authentication Server successfully decrypts the timestamp using the stored password hash, it confirms the user's identity. The AS then generates a Ticket Granting Ticket encrypted with the TGS secret key, along with a session key for communication between the client and TGS.
The TGT contains the user's identity and a session key, all encrypted so only the TGS can read it. The client also receives a copy of the session key encrypted with the user's key (so the client can decrypt it). This TGT serves as proof of authentication for subsequent service requests, eliminating the need to re-enter the password for each service access.
Ticket Granting Tickets typically have a lifetime of 10 hours by default in Active Directory, though this can be configured. The TGT is renewable up to a maximum lifetime (usually 7 days) without requiring the user to re-authenticate. This balance between security and usability allows users to access services throughout their work session while limiting the window of opportunity if a TGT is compromised.

Step 3: Service Ticket Request (TGS-REQ)
When the user needs to access a specific service (like a file server), their workstation presents the TGT to the Ticket Granting Server along with a request for the desired service. The client also sends an authenticator - a message encrypted with the TGS session key that includes the username and current timestamp - to prove possession of the legitimate session.
This step happens transparently to the user. When you try to access a shared folder, for example, your operating system automatically requests a service ticket for that file server's service. You don't have to manually perform any authentication - it all happens behind the scenes using your existing TGT.
Step 4: Service Ticket Issuance (TGS-REP)
The TGS decrypts and validates the TGT using its secret key, then checks that the authenticator is valid and current. If everything checks out, the TGS issues a service ticket encrypted with the target service's secret key. This service ticket includes the user's identity, a new session key for secure communication between the client and the service, and authorization information.
The service ticket is encrypted so only the target service can decrypt it, ensuring that even if an attacker intercepts the ticket, they cannot read its contents or use it to impersonate the user to a different service. The client also receives a copy of the service session key, encrypted so only the client can read it.

Step 5: Service Access (AP-REQ)
Finally, the client presents the service ticket to the target service along with an authenticator encrypted with the service session key. The service decrypts the ticket using its secret key, validates the user's authorization, and grants access to the requested resources.
The service checks several things: Is the ticket still valid (not expired)? Does the username in the ticket match the username in the authenticator? Is the timestamp in the authenticator current? If all checks pass, the service knows the user is legitimate and authorized, and grants access accordingly.
Once obtained, service tickets are cached on the client system. If you access the same service multiple times, your system reuses the cached ticket until it expires (typically 10 hours). This caching improves performance by eliminating repeated trips to the TGS and reduces load on the KDC infrastructure.

Step 6: Optional Mutual Authentication (AP-REP)
Kerberos doesn't just let the client prove who they are to the service - it can also work the other way around. If mutual authentication is enabled, the service responds to the client with a special message called AP-REP, encrypted using the session key they share.
When the client successfully decrypts this message, they know they're really talking to the genuine service, not an impostor. This extra step helps protect against man-in-the-middle attacks and ensures that both sides can trust each other before any sensitive information is exchanged. While optional, mutual authentication is considered a best practice for high-security environments.
- User → Authentication Server: Login request with encrypted timestamp
- Authentication Server → User: Ticket Granting Ticket and session key returned
- User → Ticket Granting Server: Ticket Granting Ticket, service request, and authenticator
- Ticket Granting Server → User: Service ticket and service session key
- User → Service: Service ticket and authenticator
- Service → User: Optional mutual authentication response

Watch the clock! Kerberos relies heavily on timestamps to prevent replay attacks. If a scenario question describes authentication failures across a network despite correct passwords, check for time synchronization issues first. If the client and server clocks differ by more than the configured tolerance (usually 5 minutes), authentication will fail.
Security Benefits of Kerberos
Kerberos provides significant security improvements over basic authentication methods. Understanding these benefits helps explain why the protocol has become the standard for enterprise authentication and why it's emphasized in the CISSP exam.
No Password Transmission
User passwords never traverse the network after initial authentication. This design dramatically reduces exposure to network sniffing attacks. Even during initial login, only an encrypted timestamp derived from the password is sent, not the password itself. If an attacker captures network traffic, they obtain only encrypted tickets that are useless without the corresponding decryption keys.
Mutual Authentication
Both clients and servers authenticate each other, preventing man-in-the-middle attacks. When mutual authentication is enabled, a client can verify it's connecting to a legitimate service, not a rogue system attempting to steal credentials or data. This bidirectional trust is critical in environments where service impersonation could lead to serious security breaches.
Replay Attack Prevention
Timestamps in all tickets and authenticators prevent replay attacks where captured authentication data might be reused maliciously. Each authenticator includes a current timestamp, and services maintain a cache of recently seen authenticators. If an attacker tries to replay a captured authenticator, the service detects the duplicate or expired timestamp and rejects the request.
The replay attack prevention mechanism depends entirely on synchronized clocks. If time synchronization fails (NTP server down, misconfigured systems), legitimate authentication requests may be rejected, causing availability issues. Conversely, if clocks are out of sync by significant amounts, the replay attack protection window may be compromised.
Centralized Credential Management
The KDC serves as a single, centralized point for credential storage and management, simplifying password policy enforcement and account administration. IT administrators can enforce consistent password policies, disable compromised accounts instantly across all services, and audit authentication attempts from a central location.
This centralization also means that password changes propagate immediately to all services without requiring synchronization across multiple systems. When a user changes their password, the KDC updates its database, and all subsequent authentication attempts use the new credentials.
Single Sign-On Capability
The single sign-on capability reduces password fatigue while maintaining security through the ticket-based system. Users authenticate once at the beginning of their session and can then access multiple services without repeated password prompts. This improves both security (users are less likely to write down passwords or choose weak ones) and productivity (less time spent entering credentials).
Support for Strong Cryptography
Modern Kerberos implementations support strong encryption algorithms including AES-256, ensuring that tickets and credentials remain secure even against sophisticated attacks. Organizations can configure which encryption types are acceptable, allowing them to disable older, weaker algorithms like DES or RC4 in favor of stronger options.
| Security Feature | Threat Mitigated | Implementation Mechanism |
|---|---|---|
| Password Protection | Credential theft via network sniffing | Passwords never transmitted; only encrypted timestamps sent |
| Mutual Authentication | Man-in-the-middle attacks | Both client and service prove identity with AP-REP messages |
| Replay Prevention | Replay attacks using captured data | Timestamps and authenticator caching detect duplicates |
| Session Security | Session hijacking | Unique session keys for each client-service pair |
| Ticket Lifetime Limits | Compromise of stolen tickets | Tickets expire after configured time period |
The security of Kerberos depends entirely on the protection of the Key Distribution Center. If the KDC is compromised, an attacker can forge tickets for any user or service in the realm. Organizations must treat KDC security with the highest priority, implementing defense-in-depth controls including network segmentation, strict access controls, comprehensive monitoring, and secure backup procedures.
CISSP Official Study Guide, 9th Edition
Conclusion
Kerberos authentication provides a robust, scalable solution for enterprise network security through its ticket-based approach, mutual authentication capabilities, and single sign-on functionality. As the primary authentication protocol for both Windows Active Directory and many Unix/Linux environments, understanding Kerberos is essential for CISSP candidates, particularly those focusing on the Identity and Access Management domain.
The protocol's design eliminates password transmission across networks, prevents replay attacks through timestamp validation, and centralizes credential management through the Key Distribution Center. While time synchronization requirements and KDC protection present operational considerations, the security benefits of Kerberos far outweigh these challenges for enterprise environments.
For CISSP exam success, focus on understanding the six-step authentication flow, the roles of the AS, TGS, and KDC, and how tickets provide secure access without password transmission. Remember that Kerberos uses symmetric encryption, requires time synchronization, and relies entirely on the security of the Key Distribution Center.
Kerberos is a network authentication protocol that uses symmetric key cryptography and a ticket-based system to enable secure, single sign-on access across enterprise networks. It operates through a Key Distribution Center (KDC) that contains both the Authentication Server (AS) and Ticket Granting Server (TGS).
Authentication Flow
The protocol follows a six-step process: AS-REQ (initial login request) → AS-REP (TGT issuance) → TGS-REQ (service ticket request) → TGS-REP (service ticket issuance) → AP-REQ (service access) → AP-REP (optional mutual authentication).
Key Components
- Authentication Server (AS): Verifies initial user credentials and issues Ticket Granting Tickets
- Ticket Granting Server (TGS): Validates TGTs and issues service-specific tickets
- Key Distribution Center (KDC): Houses both AS and TGS; stores all encryption keys
Core Security Features
- No Password Transmission: User passwords never cross the network after initial authentication
- Mutual Authentication: Both client and service verify each other's identity
- Replay Attack Prevention: Timestamps ensure authentication data cannot be reused
- Single Sign-On: Users authenticate once to access multiple services
Critical Requirements
Time Synchronization: All systems must maintain clocks synchronized within 5 minutes (typically via NTP) to prevent replay attacks. If time sync fails, authentication will fail.
KDC Security: The Key Distribution Center is a single point of failure. If compromised, attackers can forge tickets for any user or service in the realm.
Ticket Details
- TGT (Ticket Granting Ticket): Used to request service tickets; default lifetime 10 hours; renewable up to 7 days
- Service Tickets: Grant access to specific services; cached on client for performance; typically expire after 10 hours
Implementation & Standards
Microsoft Active Directory uses domain controllers as KDCs to authenticate all Windows domain logins. Modern implementations support AES-256 encryption; organizations should disable weak legacy algorithms like DES and RC4.
Common Exam Mistakes
- Confusing AS (issues TGTs after initial authentication) with TGS (issues service tickets)
- Forgetting that mutual authentication (AP-REP) is optional, not automatic
- Not recognizing the impact of time synchronization failures on availability
- Overlooking that cross-realm trust enables access between different Kerberos realms
Exam Focus: Adopt a "Think Like a Manager" mindset by identifying the KDC as a critical Single Point of Failure (SPOF). If a scenario asks about the primary disadvantage or risk of Kerberos, prioritize Availability impacts (business stoppage) and the requirement for redundancy over technical encryption details.
Challenge Yourself
Tough, realistic CISSP scenarios that expose gaps before exam day does.
Take the Challenge
